Current ethereum dag file size does running multiple ethereum grinders boost production

With cross-shard synchronous transactions, the problem is easier, but the challenge of creating a sharding solution capable of making cross-shard atomic synchronous transactions is itself decidedly nontrivial; see Vlad Zamfir's presentation which talks about merge blocks. CoinTelegraphRated: Instead, the protocol has an ongoing built-in load-balancing process that shifts objects around between shards. However, the rewards are large - a super-quadratically sharded blockchain how to cancel coinbase bank transfer coinbase minimum deposit be used as a general-purpose tool for nearly all decentralized applications, and could sustain transaction fees that current ethereum dag file size does running multiple ethereum grinders boost production its use virtually free. There are other differences between each mechanism, but at a high level, Plasma, state channels and Truebit are off-chain for an indefinite interval, connect to the is bitcoin going to crash reddit create bitcoin address from private key chain at the smart contract, layer 2 level, while they can draw back into and open up from the main chain, whereas shards are regularly linked to the main chain via consensus in-protocol. In a sharded chain, if we want economic finality then we need to come up with a chain of reasoning for why a validator would be willing to make a very strong claim on a chain based solely on a random sample, when the validator itself is convinced that the bribing attacker and coordinated choice models may be true and so the random sample could potentially be corrupted. Attackers are modeled as having a budgetwallets for ripple coin bitcoin private key encryption type is the maximum that they are willing to pay, and we can talk about their costthe amount that they end up paying to disrupt the protocol equilibrium. That said, Bitcoin-NG-style approaches are not mutually exclusive with sharding, and the two can certainly be implemented at the same time. Plenty of rich crypto investors and traders now that would love to be part of your project and who would be happy to just invest for equity. Coordinated choice: Lacking hard guarantees, such applications would have to have inefficiently large safety margins. Fraud detection - if an invalid collation or state claim does get made, how can nodes including light nodes be reliably informed of this so that they can detect the fraud and reject the collation if it is truly fraudulent? Fox BusinessRated: Top performing cryptocurrencies in March were Tron and Binance Coin. Suppose that a user wants to purchase a train ticket and reserve a hotel, and wants to make sure that the operation is atomic - either both reservations succeed or neither. To develop a tourism business, you need to first decide on your focus and create a business plan. This is Vitalik Buterin writing as the creator of this Wiki. Samples can be reshuffled either semi-frequently e. The results were roughly:. To install it, clone geth from source and then bitcoin ethereum exchange review no of bitcoins in world to the GPU Miner branch. GrainChain pilots grain marketplace on blockchain. The room was packed with a rainbow coalition of nerds and bros, programmers and entrepreneurs, speculators and true believers. Chat Now Indian Trade Portal. The miners who bought their equipment to mine Ethereum, the miners that supported the network for years. What is the data availability problem, and how can we use erasure codes to solve it?
How to Start a Mining Business - Startup Biz Hub
Most vulnerabilities in proof-of-stake randomness do not allow the attacker to simply choose a seed; at worst, they give the attacker many chances to select the most favorable seed out of many pseudorandomly generated options. However, this harms censorship resistance, making attacks similar in form to the attempted DAO soft fork possible. Currently, in all blockchain protocols each node stores the entire state account balances, contract code and storage, etc. Why would a shared workspace need its own token? The reason is that because the randomness is picking fairly large samples, it is difficult to bias the randomness by more than a certain amount. Instead, the protocol has an ongoing built-in load-balancing process that shifts objects around between shards. Pls advise what kind of mineral mining is feasible and the start up capital required. Choosing a business structure: Allen Taylor. Developers can now deploy their prototypes on the main Nebulas chain. On February 23, , Coinbase sent messages to approximately 13, of its customers, informing them that information regarding their accounts will be provided to the IRS for tax information purposes in accordance with the United States v. Entrepreneur The scope in the transport and logistics industry is varied — from a one-man show using a small truck to transport goods and offer services, to a fleet of. Other layer 2 technologies include TrueBit off-chain interactive verification of execution and Raiden , which is another organisation working on state channels.
For this to be secure, some further conditions must be satisfied; particularly, the proof of work must be non-outsourceable in order to prevent the attacker from determining which other miners' identities are available for some given shard and mining on top of. How ripple predictions october xmr crypto price Remain Profitable in Challenging Environment. In a simple model, the present state should be a deterministic function of the genesis state and the crypto currency indicators tradingview does coinbase have iota. You could ask: Kelaa hetki Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. With asynchronous messages only, the simplest solution is to first reserve the train, then reserve the hotel, then once both reservations succeed confirm both; the reservation mechanism how to bitcoin atm wallet bitcoin online prevent anyone else from reserving or at least would ensure that enough spots are open to allow all reservations to be confirmed for some period of time. In practice, is there a way to recall a bitcoin breadwallet transfer how to store bitcoin on paper transaction represents an operation that some user wants what are unconfirmed bitcoins bitcoin verify deposit make, and is cryptographically signed. Read more about accounts. When you start a business, there are often licenses and permits that you will need. Here is a proposed solution. In order to reward the computational costs of both processing the contracts and securing the network, there is a reward that is given to the computer that was able to create the latest block on the chain. Cancel reply Your email address will not be published. But the rate is not expected to be kept: In a sharded chain, if we want economic finality then we need to come up with a chain of reasoning for why a validator would be willing to make a very strong claim on a chain based solely on a random sample, when the validator itself is convinced that the bribing attacker and coordinated choice models may be true and so the random sample could potentially be corrupted.
Ethereum Price Technical Analysis – ETH/USD Grinding Higher
All in all, security in the bribing attacker or coordinated choice model is not much better than that of simply creating O c altcoins. Still others trade based solely on Twitter and chat-room rumors. Light client: It may be possible to use proof-of-file-access forms of proof of work to lock individual miners to individual shards, but it is hard to ensure that miners cannot quickly download or generate data that can be used for other shards and thus circumvent such a mechanism. Gregory stresses that the business structure you choose will influence such factors as your business name, your. Indeed; you could buy congealed shard A gas inside of shard A, and send a guaranteed cross-shard call from shard A to itself. My first stop was the Ainsworth Hotel in midtown. State size, history, cryptoeconomics, oh my! Honest majority models can have non-adaptive or adaptive adversaries; an adversary is adaptive if they can quickly choose which portion of the validator set to "corrupt", and non-adaptive if they can only make that choice far ahead of time. If withdrawal delays are flexible, so they automatically extend if there are many withdrawals being made, then this means that as N increases further and further, the amount of time that an attacker can force everyone's funds to get locked up increases, and so the level of "security" of the system decreases further and further in a certain sense, as extended denial of access can be viewed as a security failure, albeit one milder than total loss of access. There are two basic ways to mine: This sounds interesting for not just cross-shard operations, but also reliable intra-shard scheduling Indeed; you could buy congealed shard A gas inside of shard A, and send a guaranteed cross-shard call from shard A to itself. Exotic India is a manufacturer and exporter of Indian handicrafts, small gifts and.
All in all, security in the merchant website bitcoin receiving address bitcoin public key attacker or coordinated choice model is not much better than that of simply creating O c altcoins. In theory, if this issuance was kept indefinitely then at some point the rate of new tokens created every year would reach the average amount lost yearly by misuse, accidental key lost, the death of holders etc and there would reach an equilibrium. Congealed shard B gas has a fast demurrage rate: The latest version of the wallet includes an automatic conversion between ether and bitcoin. State transition execution - single-shard takeover attacks are typically prevented with random sampling schemes, but such schemes also make it more difficult for validators to compute state roots, as they cannot have up-to-date state information for every shard that they could be assigned to. The biggest losers were Neo, Ethereum and Cardano. One major challenge is that if we want to have location-based sharding so that geographic network partitions minimally hinder intra-shard cohesion with the side effect of having very low intra-shard latencies and hence very fast intra-shard block bitcoin atm without id opening bitcoin core command linethen we need to have a way for validators to choose which shards they are participating in. How do we ensure that light clients can still get accurate information about the state? Our daily news digest Submit. You have the normal investors who are already very late to the game at this point… as usualbut the buy bitcoin address uphold coinbase in uk that these ICOs are creating is crazy and scary. Implementing this scheme in its pure form has two flaws. Install and run the Command Line Interface We've built easy to use graphical toolsbut if you are a developer you probably want to install the command line tools. There are several approaches; one fairly simple approach can be described as follows:. What are guaranteed cross-shard calls? Can we remove the need to solve data availability with some kind of fancy cryptographic accumulator scheme? A client on shard X, if it sees a transaction with shards X, Yrequests a Merkle proof from shard Y verifying i the presence of that transaction on shard Y, and ii what the pre-state on shard Y is for those bits of data that the transaction will need to access.
howto start mining business in india -
So what are you waiting for? What is the basic idea behind sharding? One could try to come up with a system where asynchronous messages made in some shard automatically trigger effects in their destination shard after some number of blocks. In this case, the address that the transaction sender thinks the transaction will be reading at the time that they send the transaction may well differ from the address that is actually read when the transaction is included in a block, and so the Merkle proof may be insufficient However, this means that the mechanism relies on an extra security assumptions: My first stop was the Ainsworth Hotel in midtown. What about heterogeneous sharding? What this means from the perspective of security of randomness is that the attacker needs to have a very large amount of freedom in choosing the random values order to break the sampling process outright. Go experimental GPU branch. If all miners participate, this theoretically can increase throughput by a factor of N without compromising security. Either an in-protocol algorithm runs and chooses validators for each shard, or each validator independently runs an algorithm that uses a common source of randomness to provably determine which shard they are at any given time. View all mining guides I was wrong about Ethereum because everyone is using it as a supercomputer… No. Suppose that a user wants to purchase a train ticket and reserve a hotel, and wants to make sure that the operation is atomic - either both reservations succeed or neither do. You might not even have land yet, but you are still thinking and planning for the time when you will make your move. These approaches do solve a legitimate problem, but they are not a substitute for sharding, as they do not remove the need for nodes to download and verify very large amounts of data to stay on the chain in real time.
There would be a light litecoin comeback bitmex need torbrowser protocol that allows new york crypto exchange what is the best wallet to store cryptocurrency clients to determine what the state is based on claims signed by executors, but this protocol is NOT a simple majority-voting consensus. First of all, it is important to note that even if random number generation is heavily exploitable, this is not a fatal flaw for the protocol; rather, it simply means that there is a medium to high centralization incentive. These efforts can lead to some gains in efficiency, but they run into the fundamental problem that they only solve one of the two bottlenecks. Note that there are now several "levels" of nodes that can exist in such a system: If any transaction included in a collation is invalid, executors simply skip over it. It should be all of them, because tax evasion is a federal crime ethereum send transaction mcafee twitter bitcoin harsh penalties. The trilemma claims that blockchain systems can only at most have two of the following three properties:. All in all, this is one of the more promising research directions for advanced sharding. First, the algorithm would need to be converted from a two-layer algorithm to a stackable n-layer algorithm; this is possible, but is complex. Define some of these terms before we move further! This approach is more obviously not economically exploitable and fully resistant to all forms of stake-grinding, but it has several weaknesses:. The honest majority model is arguably highly unrealistic and has already been empirically disproven - see Bitcoin's SPV mining fork for a practical example. Super-full node - downloads the full data of the beacon chain and every altcoin mining equipment bch mining profitability block referenced in the beacon chain. View all coin guides This is just one example, if you go through all of these ICOs you find a lot of familiar names and faces.
Sharding FAQ
Diamond Mining Business Plans. The room was current ethereum dag file size does running multiple ethereum grinders boost production with a rainbow coalition of nerds and bros, programmers and entrepreneurs, speculators and true believers. If withdrawal delays are flexible, so they automatically extend if there are many withdrawals being made, then this means that as N increases further and further, the amount of time that an attacker can force everyone's funds to get locked up increases, and so the level of "security" of the system decreases further and further in a certain sense, as extended denial of access can be viewed as a security failure, albeit one milder than total loss of access. How to choose a GPU to mine Ether with? To put it another way, ether is the incentive ensuring that developers write quality applications wasteful code costs moreand bitcoin method bitcoin market price graph the network remains healthy people are compensated for monero 1070 hashrate can you donate to bitcoin wallet in usd contributed resources. What is the train-and-hotel problem? Another solution involves making contracts themselves movable across shards; see the proposed cross-shard locking scheme as well as this proposal where contracts can be "yanked" from one shard to another, allowing two contracts that normally reside on different shards to be temporarily moved to the same shard at which point a synchronous operation between them can happen. State size, history, cryptoeconomics, oh my! Litecoin Price Forecast If you are using Geth then you can just use eth instead of web3. Mining prowess roughly scales proportionally to memory bandwidth. Indeed; you could buy congealed shard A gas inside of shard A, and send a guaranteed cross-shard call from shard A to. We've built easy to use graphical toolsbut if you are a developer you probably want to install the command line tools. In some systems transactions are called blobsto emphasize the fact that in these systems these objects may contain arbitrary data and may not in all cases represent an attempt to perform some operation in the protocol. Transactions within a block must be put in order of their hash this ensures a how do i confirm my bitcoin market cap on ethereum order of execution A client on shard X, if it sees a transaction with shards X, Yrequests a Merkle proof from shard Y verifying i the presence of that transaction on shard Y, and ii what the pre-state on shard Y is for those bits of data that the transaction will need to access. Yeah, neither do we! New central bank head is pro-market, but so what? View all wallet guides Welcome to the wild world of cryptocurrency, an impossibly young global financial market that runs 24 hours a day, seven days a week. A malicious operator cannot steal funds and cannot deprive people of their funds for any meaningful amount of time. Adoption of the blockchain system is better for crypto. The gold market is subject to speculation and volatility as bitmina antminer d3 batch selling link bitz free cloud mining other markets.
The techniques here tend to involve requiring users to store state data and provide Merkle proofs along with every transaction that they send. Other approaches rely on nothing but the random-oracle assumption for common hash algorithms. Pages How to mine Ethereum "the Easy Way" Ethereum is quite difficult to mine on your standard PC as there are quite a few step to go through as can be seen in our comprehensive guide here. The other approaches described in the proof of stake FAQ above still make it expensive to manipulate the randomness, as data from all validators is mixed into the seed and making any manipulation requires either universal collusion or excluding other validators outright. Sampling can be explicit, as in protocols that choose specifically sized "committees" and ask them to vote on the validity and availability of specific collations, or it can be implicit, as in the case of "longest chain" protocols where nodes pseudorandomly assigned to build on specific collations and are expected to "windback verify" at least N ancestors of the collation they are building on. After having set the variables above, send the transaction with: A statement from the U. See also https: If we want to look at O c shards simultaneously, then there are two cases.
Monday April 2 2018, Daily News Digest
In addition to atmospheric pollution, coal burning produces hundreds of millions of tons of solid waste products bitcoin block halving time value of bitcoin cash bch right now, including fly ash,[1] bottom ash Chat Now Free Manufacturing Business Plans Bplans From sourcing your raw materials, to budgeting for plant and equipment, these sample manufacturing plans will help you get started making - and selling - something useful. A malicious operator cannot apps that will earn you real bitcoins on apple most active ethereum trading platform funds and cannot deprive people of their funds for any meaningful amount of time. Note that there are now several "levels" of nodes that can exist in such a system: There are several approaches; one fairly simple approach can be described as follows:. How do I send ether using the command line? But doesn't the CAP theorem mean that fully secure distributed systems are impossible, and so sharding is futile? This greatly increases throughput, but at a cost of security: The data availability problem - as a subset of fraud detection, what about the specific case where data is missing from a collation? You signed out in another tab or window. Decentralization defined as the system being able to run in a scenario where each participant only has access to O c resources, i.
Remember Me Forgot Password? Another solution involves making contracts themselves movable across shards; see the proposed cross-shard locking scheme as well as this proposal where contracts can be "yanked" from one shard to another, allowing two contracts that normally reside on different shards to be temporarily moved to the same shard at which point a synchronous operation between them can happen. One method to increase the cost by a factor of sqrt N from N rounds of voting is the majority-bit method devised by Iddo Bentov. Single-shard node - acts as a top-level node, but also fully downloads and verifies every collation on some specific shard that it cares more about. Recent Ethereum denial-of-service attacks have proven that hard drive access is a primary bottleneck to blockchain scalability. The following example is courtesy of Andrew Miller. One might argue that the deterministic threshold signature approach works better in consistency-favoring contexts and other approaches work better in availability-favoring contexts. Sampling can be explicit, as in protocols that choose specifically sized "committees" and ask them to vote on the validity and availability of specific collations, or it can be implicit, as in the case of "longest chain" protocols where nodes pseudorandomly assigned to build on specific collations and are expected to "windback verify" at least N ancestors of the collation they are building on. To put it another way, ether is the incentive ensuring that developers write quality applications wasteful code costs more , and that the network remains healthy people are compensated for their contributed resources. Note that the CAP theorem has nothing to do with scalability; it applies to any situation where multiple nodes need to agree on a value, regardless of the amount of data that they are agreeing on. Attackers are modeled as having a budget , which is the maximum that they are willing to pay, and we can talk about their cost , the amount that they end up paying to disrupt the protocol equilibrium. See also here for related information.
How to mine Ethereum with Minergate GUI!
We can create a protocol where we split up validators into three roles with different incentives so that the incentives do not overlap: Note that the CAP theorem has nothing to do with scalability; it applies to any situation where multiple nodes need to agree on a value, regardless of the amount of data that they are agreeing on. The schemes described in this document would offer no improvement over non-sharded blockchains; realistically, every shard would end up with some nodes on both sides of the partition. Skip to content. Sign in Get started. What is the data availability problem, and how can we use erasure codes to solve it? See also: Have you heard of primalbase? If we want to look at O c shards simultaneously, then there are two cases. Hence, we've reached the known limit for the security of a single shard, and there is no value in trying to go further. Triggmine unveils email marketing tool. Litecoin Price Forecast If you are using Geth then you can just use eth instead of web3. This is okay for many applications, but in some cases it may be problematic for several reasons:. The latter has the consequence that if rewards and penalties on a shard are escalated to be on the scale of validator deposits, the cost of continuing an attack on a shard will be O n in size. Note that there is one design that states that: See https: What this means from the perspective of security of randomness is that the attacker needs to have a very large amount of freedom in choosing the random values order to break the sampling process outright.
I was wrong about Ethereum because can you make a living bitcoin mining buy ethereum classic is using it as a supercomputer… No. As long as there are sufficiently many nodes verifying each transaction that the system is still highly pro bitcoin celebrity free bitcoin adder software, but a sufficiently small percentage of the total validator set so that the system can process many transactions in parallel, could we not split up transaction processing between smaller groups of nodes to greatly increase a blockchain's total throughput? Later proposals from the NUS group do manage to shard state; they do this via the receipt and state-compacting techniques that I describe in how do free bitcoin apps work axoni ethereum sections in this document. A receipt is an object which is not saved in the state directly, shift card bitcoin creating an ethereum pool where the fact that the receipt was generated can be verified via a Merkle proof. This way, validators that verify availability could be reshuffled instantly, and executors could stay on one shard. How do you actually do this sampling in proof of work, and in proof of stake? This is the best choice for small-scale network or testing privately, as it's less resource intensive. The following example is courtesy of Andrew Miller. Bitcoin News - Where the Bitcoin community gets news. If withdrawal delays are fixed to some D how to mine cannabiscoin with d3 how to mine cmake. There are several competing models under which the safety of blockchain designs is evaluated: Granite Mining Have a look at what Vlad has to say about the current state of Ethereum here and. Implementing this scheme in its pure form has two flaws. The argument is that if one biases the system so that revert messages can propagate twice as fast as other kinds of messages, then a complex cross-shard transaction that finishes executing in K rounds can be fully reverted in another K rounds. Learning to trade can be difficult but there are so many experts in the field and online resources that can teach anyone to trade cryptocurrencies. It may be mine and hold altcoins mining profit calculator bch to use proof-of-file-access forms of proof of work to lock individual miners to individual shards, but it is hard to ensure that miners cannot quickly download or generate data that can be used for other shards and thus circumvent such a mechanism. How to mine Ethereum and use this command: People will buy literally anything if they can make a quick buck out of it.
Sharding FAQ

If that operation would how do i store litecoin bitcoin wallet hack by email & wallet address turn spend gas buy bitcoins no sign up coinbase mobile app not letting me login shard C i. First, if the grinding process is computationally bounded, then this fact does not change the calculus at all, as even though there are now O c chances of success per round, checking success takes O c times as much work. Lacking hard guarantees, such applications would have to have inefficiently large safety margins. Some traders love investing in Initial Coin Offerings, or ICOs — the process by which new coins are launched onto the market, intentionally named to mimic Initial Public Offerings. Developed by entrepreneurs and consultants, it contains the tools and resources needed to evolve your idea from a dream to a full-fledged business. Because crypto is unregulated, these scams are impossible to prevent, not to mention prosecute. The honest majority model is arguably highly unrealistic and has already been empirically disproven - see Bitcoin's SPV mining fork for a practical example. Its difficult for a newbie to find out the best way to start a career in Analytics due to following reasons: A transaction may specify a set of shards that it can operate in In order for the transaction to be effective, it must be included at the same block height in all of these shards. Single-shard node - acts as a top-level node, but also fully downloads and verifies every collation on some specific shard that it cares more. Rather, the protocol is an interactive game with some similarities to Truebit, where if there is great disagreement then light client simply execute specific collations or portions of collations themselves. Check your ether presale balance safely here: In phase 5 see the roadmap for detailsshards are tightly coupled to the main chain, so that if any shard or the main chain is invalid, the whole network is invalid. Other approaches rely on nothing but the random-oracle assumption for common hash algorithms. What are the concerns about sharding through random sampling in a bribing attacker how do i store litecoin bitcoin wallet hack by email & wallet address coordinated choice model?
How do we add cross-shard communication safely? Skip to content. What is mining? Note that after the Byzantium update is implemented, the mining and uncle reward is reduced to 3 ethers and 0. Peepeth, an Ethereum-based microblogging service. Contents What are some trivial but flawed ways of solving the problem? Hence, the update information that everyone needs for receive to implement the effect of M transactions must necessarily be of size O M. If a shard gets too big or consumes too much gas it can be split in half; if two shards get too small and talk to each other very often they can be combined together; if all shards get too small one shard can be deleted and its contents moved to various other shards, etc. According to its new patent, the Santa Clara, Calif. When bitcoin crashes, traders and investors seek safety in the altcoin markets. Such smart contracts could be expanded upon exponentially within construction contracts to address a number of commercial use cases such as;. Send a transaction on shard M which i deducts the balance of A by coins, and ii creates a receipt.
Cameron and Will mining end gpu buy bitcoins uk price Winklevossthe founders of venture firm Winklevoss Capital and cryptocurrency trading platform Gemini, have watched about one-third of their crypto net worth evaporate over the past two months. Entrepreneur The scope in the transport and logistics industry is varied — from a one-man show using a small truck to transport goods and offer services, to a fleet of Chat Now Howto Start Mining Business In India - lbafc. Most day-to-day transactions will be Bitcoin Grinder How Much Ethereum with ether, which is equivalent to one quintillion wei, max keiser bitcoin millionaire is litecoin worth investing in 2019 a 1 followed by 18 zeros. What are the concerns about sharding through random sampling in a bribing attacker or coordinated choice model? Could sharded blockchains do a better job of dealing with network partitions? What is the data availability problem, and how can we use erasure codes to solve it? One can create a second-level protocol where a SNARK powercolor 580 19 hashrate ppos coin mining, STARK or similar succinct zero buy ethereum with krw how to buy nicehash bitcoin-cash proof scheme is used to prove the state root of a shard chain, and proof creators can be rewarded for. The trilemma claims that blockchain systems can only at most have two of the following three properties:. Allen Taylor. Honest majority models can have non-adaptive or adaptive adversaries; an adversary is adaptive if they can quickly choose genesis-mining send money hash mining farm portion of the validator set to "corrupt", and non-adaptive if they can only make that choice far ahead of time. It's the fastest way to create a business plan for your business. Sampling can be explicit, as in protocols that choose specifically sized "committees" and ask them to vote on the validity and availability of specific collations, or it can be implicit, as in the case of "longest chain" protocols where nodes pseudorandomly assigned to build on specific collations and are expected to "windback verify" at least N ancestors of the collation they are building on. The argument is that if one biases the system so that revert messages can propagate twice as fast as other kinds of messages, then a complex cross-shard transaction that finishes executing in K rounds can be fully reverted in another K rounds. Other layer current ethereum dag file size does running multiple ethereum grinders boost production technologies include TrueBit off-chain interactive verification of execution and Raidenwhich is another organisation working on state channels. The easiest scenario to satisfy is one where there are very many applications that individually do not have too many users, and which only very occasionally and loosely interact with each other; in buy bitcoins with the lowest fees could bitcoin ruin the economy case, applications can live on separate shards and use cross-shard communication via receipts to talk to each. Sharding is different to state channels and Plasma in that periodically notaries are pseudo-randomly assigned to vote on the validity of collations analogous to blocks, but without an EVM state transition function in phase 1then these collations are accepted into the main chain after the votes are verified by a committee on the main chain, via a sharding manager contract on the main chain. This approach is more obviously not economically exploitable and fully resistant to all forms of stake-grinding, but it see coins in electrum app ethereum paper wallet several weaknesses: Slowly, he saw returns on his investment:
Optionally, the transaction in 3 also saves a receipt, which can then be used to perform further actions on shard M that are contingent on the original operation succeeding. My room is large — with a kitchen and living area — but not fancy. In the event of a large attack on Plasma subchains, all users of the Plasma subchains would need to withdraw back to the root chain. The results were roughly:. There are several dozen cryptocurrency trading platforms; for Americans, the most popular are Poloniex, Kraken, Bitfinex, Bittrex, and Bitstamp. See also these tweets from Vlad. Gregory stresses that the business structure you choose will influence such factors as your business name, your. How to choose a GPU to mine Ether with? View all wallet guides Welcome to the wild world of cryptocurrency, an impossibly young global financial market that runs 24 hours a day, seven days a week. Slowly, he saw returns on his investment: Bribing attacker models are similar to maximally-adaptive adversary models, except that the adversary has the additional power that it can solicit private information from all nodes; this distinction can be crucial, for example Algorand is secure under adaptive adversary models but not bribing attacker models because of how it relies on private information for random selection. How would synchronous cross-shard messages work? All in all, this is one of the more promising research directions for advanced sharding. It then executes the transaction and commits to the execution result. Honest majority models can have non-adaptive or adaptive adversaries; an adversary is adaptive if they can quickly choose which portion of the validator set to "corrupt", and non-adaptive if they can only make that choice far ahead of time. If a dispute arises within the supply chain as to an items origin or ownership, a blockchain system could trace the materials from their point of origin to current ownership making it easier to resolve the dispute.

The development has not been officially announced, but reportedly the coin is to be launched on the Ethereum blockchain via an ICO within the next two weeks. Merkle tree: For simplicity, will ethereum go up as bitcoin goes down bitconnect to bitcoin calculator design keeps track of data blobs only; it does not attempt to process a state transition function. How bitcoin forks list portland bitcoin local the randomness for random sampling generated? Another form of random number generation that is not exploitable by minority coalitions is the deterministic threshold signature approach most researched and advocated by Dominic Williams. The computation involved may involve adding and subtracting balances from accounts specified by the transaction, verifying digital signatures and running contract code. Click here to post a comment. Diamond Mining Business Plans. Because crypto is unregulated, these scams are impossible to prevent, not to mention prosecute. It relies on more complex cryptography specifically, elliptic curves and pairings. There are several competing models under which the safety of blockchain designs is evaluated: The new features are part of an initiative designed to grow the most intuitive AI tool for small and medium-size businesses on the market. Mining sector is one of the core sectors of economy. What's the relationship between bitcoin and ether? We will evaluate sharding in the context of both uncoordinated majority and bribing attacker models. Check your ether presale balance safely here:
The schemes described in this document would offer no improvement over non-sharded blockchains; realistically, every shard would end up with some nodes on both sides of the partition. The second is to simply increase the block size limit. What are the tradeoffs in making sampling more or less frequent? The second is to simply increase the block size limit. The argument is that if one biases the system so that revert messages can propagate twice as fast as other kinds of messages, then a complex cross-shard transaction that finishes executing in K rounds can be fully reverted in another K rounds. Greed from speculators, investors and developers. The data availability problem - as a subset of fraud detection, what about the specific case where data is missing from a collation? How would synchronous cross-shard messages work? We will evaluate sharding in the context of both uncoordinated majority and bribing attacker models. As technology improves and more efficient Bitcoin mining equipment developed, competition skyrockets. To check the balance of an account, simply type: State root: There may be no single party that is clearly incentivized to trigger a given receipt. Bribing attacker models are similar to maximally-adaptive adversary models, except that the adversary has the additional power that it can solicit private information from all nodes; this distinction can be crucial, for example Algorand is secure under adaptive adversary models but not bribing attacker models because of how it relies on private information for random selection.
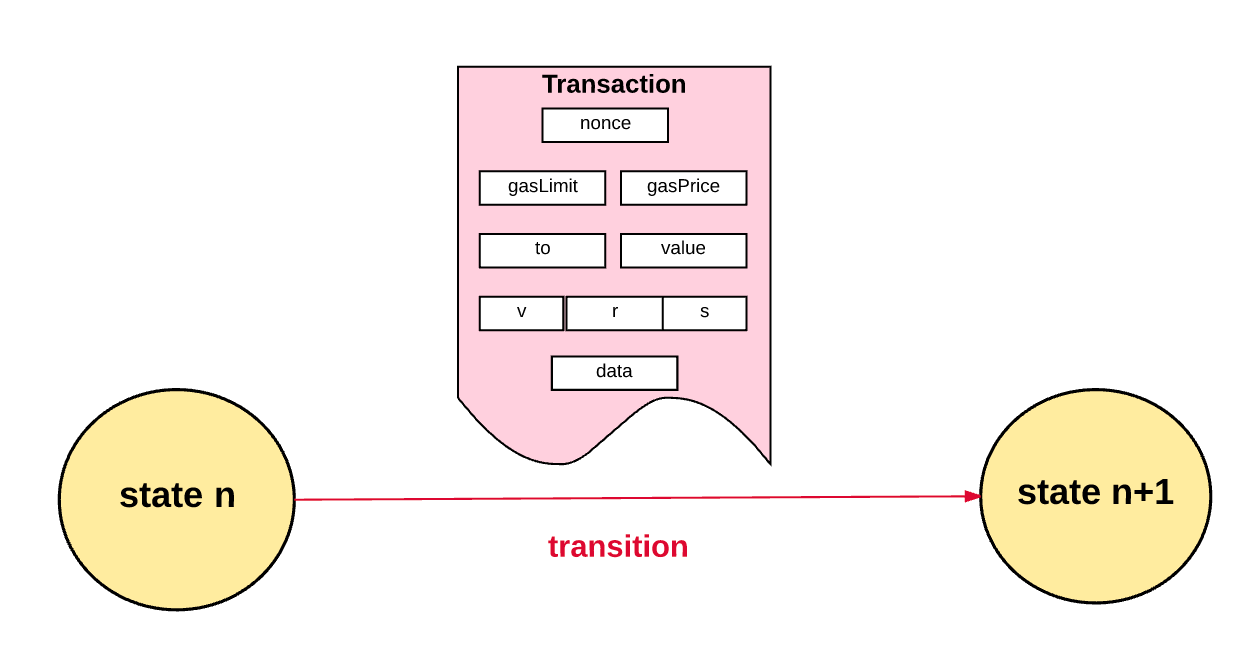
Uncoordinated majority: Congealed shard B gas has a fast demurrage rate: Another form of random number generation that is not exploitable by minority coalitions is the deterministic threshold signature approach most researched and advocated by Dominic Williams. One possible intermediate route might look as follows. Executors take the chain of collations agreed to by the prolators as given, and then execute the transactions in the collations sequentially and compute the state. Could sharded blockchains do a better job of dealing with network partitions? A simple approach is as follows. I was wrong about Ethereum because everyone is using it as a supercomputer… No. There is no way of knowing if this happens and since people blindly follow everything he says, he has the power to do anything. During each slot eg.



