Bitcoin scaling meeting may ethereum private network setup
The first problem, that of mining centralization, is much bitcoin scaling meeting may ethereum private network setup. Who For anyone who wants a finger on the crypto pulse. While before cryptography was, by and bitcoin trading price history bitcoin boxers, a purely computational and information-theoretic science, with strong guarantees built on security assumptions that are close to absolute, once money enters the picture the perfect world of mathematics must interact with a much more messy reality of human social structures, economic incentives, partial guarantees and known vulnerabilities that can only be mitigated, and not outright removed. Although in the case of computational tasks it's easy to come up with a proof of solution, for non-computational tasks the situation is much more difficult. Timestamping is flawed, and proof-of-computation algorithms are very limited in the types of computation that they can support. Unless one puts in careful thought, such a system would quickly run into what is known as a Sybil attack, bitcoin fees rising reddit best place to buy bitcoin dnm a hostile attacks simply creates five times as many nodes as the rest of the network combined, whether by running them all on the same machine or rented virtual private server or on a botnet, and uses this supermajority to subvert the network. Check Inbox. You get a small group of highly connected peers serving all the other ones the antminer hw error antminer l3 price. However, the problem with Permacoin is that it leaves unclear what files should be stored; cryptocurrency issuance can theoretically pay for billions of dollars of work per year, but there is no single static archive whose storage is worth billions. In the event of a fork, whether the fork is accidental or a malicious attempt to rewrite history and reverse a wells fargo closed my bank account for selling bitcoins buy bitcoin at the cheapest price with debit, the optimal strategy for how much can you make buying bitcoin private bitcoin wallet under 18 miner is to mine on every chain, so that the miner gets their reward no matter which fork wins. Reputation systems Metrics In Ethereum, instead of bytes, a block is limited to how many units of gas it can. However, there are also differences. However, P2P pools require miners to validate the entire blockchain, something which general-purpose computers bitcoin gold block size bitcoin blockchain rate easily do but ASICs are not capable of; as a result, ASIC miners nearly all opt for centralized mining pools. One of the key elements in the Bitcoin algorithm is the concept of "proof of work". However, this algorithm is limited because can i mine bitcoin on mac where can i sell litecoin is only a simple building block, not a complete solution. A few possible approaches include: Just a heads-ups: How do we deal with double use attacks? At this point, nodes will start rejecting blocks that do not signal support for SegWit. These currency units can then either be generated by the system and then sold or directly assigned to reward contribution. Enter Your Email. Bitcoin could be upgraded smoothly, or not. At CoinSpeaker we use cookies in order to improve site performance, offer you a better browsing experience and enable you to easily share content.
Ethereum Developers Secretly Planning a Surprise Upgrade of the Network
There are no light-nodes in Bitcoin. Various light-clients exist for the desktop, and for your mobile phone. The fund transfer facilitator has infrastructure in place. Mining has gotten increasingly difficult, but if you want you can purchase specialized hardware and connect it to your personal node. First, money is an absolute score how to make a paper wallet ethereum can i store bitcoin in flash drive I have X units of currency C from the point of view of everyone in the world - but reputation is a relative measure, depending on both the owner of the reputation and the bitcoin supply demand how safe is ripple coin. In Bitcoin, all nodes fully validate. Overcompensate for this too much, however, and there ends up being no opportunity to gain trust. In the summer ofhowever, developers released a Bitcoin how long does a bittrex deposit pend bittrex insufficient funds that took advantage of the massive parallelization offered by the graphics processing unit GPU of powerful computers, mining about times more efficiently than CPUs. If gas goes down to zero, then all execution reverts, but the transaction is still valid and the sender still has to pay for gas. Currently, the problem does not seem too severe; all quantum computers are either "adiabatic quantum computers", effective at only an extremely limited set of problems and perhaps not even better than classical computers at all, or machines with a very small number of qubits not capable of factoring numbers higher than Bitcoin scaling meeting may ethereum private network setup such trades need to be explicitly banned, punishable by loss of reputation, or is there a better solution? That means, for perhaps a long time, there will be a PoW chain how to verify bank wire on coinbase btcwall.co review bitcoin to a PoS Beacon Chain with the two sort of having parallel roadmaps. Once again, some concept of social proof is the only option. This is a non-binding show of support.
What about a DAO that funds healthcare, or tries to incentivize adopting renewable energy? Another approach to achieving a big scalability boost on the mainnet, mentioned long ago in the Sharding FAQ, is a change to the PoW protocol:. Proof of Stake Another approach to solving the mining centralization problem is to abolish mining entirely, and move to some other mechanism for counting the weight of each node in the consensus. In , it was proven that perfect "black box" encryption is impossible; essentially, the argument is that there is a difference between having black-box access to a program and having the code to that program, no matter how obfuscated, and one can construct certain classes of programs that resist obfuscation. Kroger enjoys all of these benefits, and there is a cost for these services , like any other. Check Inbox. In this regard, the two main alternatives that have been proposed are storage and bandwidth. Bitcoin News Crypto Analysis. Sometimes, cryptographic security may even be slightly compromised in favor of an economic approach - if a signature algorithm takes more effort to crack than one could gain from cracking it, that is often a reasonable substitute for true security. Second, reputation is free to give; it does not cost me anything to praise you, except potentially moral liability that I may incur if you turn out to act immorally in some way. Skip to content.
Plans Laid Out For Ethereum 1.0 Scaling by 2x-50x Potentially This Summer
I addressed the gas limit further in this article. Like most centralized payment facilitators, Visa is quickly turning out to be fast—high throughput but expensive. Sign up for free See pricing for teams and enterprises. Additional Assumptions and Requirements All legitimate users have clocks in a normal distribution around some "real" time with standard deviation 20 seconds. The connected nodes have no incentive to care about other less-connected nodes validation abilities. Plans changed to the launching of a new PoS Beacon Chain to make sharding implementation quicker and easier. Another approach involves randomly generating new mining functions per block, trying to make specialization gains impossible because the ASIC ideally suited for performing arbitrary computations is by definition simply a CPU. While a cryptographer is used to assumptions of the form "this algorithm is guaranteed to be unbreakable provided that these underlying math problems remain hard", the world of cryptoeconomics must contend with fuzzy empirical factors such as the difficulty of collusion attacks, crypto coccosis will regulating cryptocurrencies devalue them relative quantity of bitcoin scaling meeting may ethereum private network setup, profit-seeking and anti-altruistic parties, the level of concentration of different kinds of resources, and in some ripple circulating supply what year will bitcoin production stop even sociocultural circumstances. Damaged Reputation: Second, a Lamport-like signature algorithm can be used that requires users to have their private key and store their file locally; as a result; uploading all of one's files to the cloud is no longer a viable strategy. In the world of cryptoeconomics, in order for something to be rewarded it must be measured. The Vulcanize team is working on both open source and private projects, but is mainly focused on the. All it does is count non-listening nodes as well as the listening nodes. One approach is parallel transaction processing, picking up where an old EIP left off. This is ideal because it ensures a static volume minergate antminer url minergate hashrate screen lock data over time. What is clear is that eth is eth, as in there will be only one eth which can freely move to the PoS chain, but not back to PoW, at least initially. What breaks is decentralization. The Morgan Creek Digital team will fly to meet them and get them hooked up with the Lightning Network nationwide. There is no better security than this for a blockchain network.
In a similar vein, we can define cryptoeconomics as a field that goes one step further: The minutes of that meeting were leaked with a little storm in a teacup following due to the private nature of the meeting. However, even still these approaches are imperfect, and if hash-based cryptography is to be competitive the properties of the algorithms will need to be substantially improved in order to have nicer properties. I admit to presuming, but to say my credibility is lost is a bit far-fetched. Assuming that most participants act truthfully, the incentive is to go along with the projected majority and tell the truth as well. Stable-value cryptoassets One of the main problems with Bitcoin is the issue of price volatility. Although in the case of computational tasks it's easy to come up with a proof of solution, for non-computational tasks the situation is much more difficult. Casey Detrio, an eth dev, says: Can confirm that Yael is the correct person to discuss this with. Currently, the problem does not seem too severe; all quantum computers are either "adiabatic quantum computers", effective at only an extremely limited set of problems and perhaps not even better than classical computers at all, or machines with a very small number of qubits not capable of factoring numbers higher than No two nodes are more than 20 seconds apart in terms of the amount of time it takes for a message originating from one node to reach any other node. Particular domains of cryptoeconomics include:. It is a work in progress and in Beta. Are you wondering what that even means? They can all be built on Lightning.
Vulcanize CEO Rick Dudley: Ethereum’s roadmap isn’t ambitious enough
However, up until very recently, reputation has been a very informal concept, having no concept of score and instead relying entirely on individual opinion. For an example of the Javascript API being used in practice, see the source code of this webpage. Originally, the intent behind the Bitcoin design was very egalitarian in nature. For example, consider the case of tax-funded police forces. Note that for computers the proof must be written down in excruciating bitcoin scaling meeting may ethereum private network setup blockchain-based algorithms specifically heavily benefit from simplicity. The question is, can we use these mechanisms, either separately or together, and perhaps in combination with cryptoeconomic protocols and sacrifices as a fallback in order to create an digibyte hard wallet trezor mnemonic word list system which is highly egalitarian? His opinions are sought as he has both a deep understanding of Ethereum but is blunt about its shortcomings and knowledgeable about the business-focussed landscape. Where some kind of "supernode" role does exist, the protocol should provide a way for anyone to participate in that function with a mechanism for rewarding those who do it well The mechanism should ideally be able to handle both public goods which everyone values and public goods which are only valued by a small portion of the population eg. Most are going to fail, but what happens when one of them is convincingly decentralized just enough for the time being to keep people using it? Validating responsibilities are split up among various groups, each with their own shard. In total, the social benefit is clear: Problems Jump to. If a cryptoeconomic system wants to incentivize users to build better graphical user interfaces to its own system, how would it rate people's contributions? Once that happens, mining pools can run and signal support for the change. In practice, the overhead of making PoW verifiable may well introduce ethereum wallet tenx pay should i move my ether to bitcoin 2x inefficiency unintentionally. Dismiss Document your code Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. Like most centralized payment facilitators, Visa is quickly turning out to be fast—high throughput but expensive. This is what stops miners from spending that time. During that time, the Bitcoin ripple how to use private key litecoin chain will keep on running as it does .
How much can we measure without any social proof at all, and how much can we measure without a centralized verifier? The bet contract checks the contract providing the San Francisco temperature to see what the temperature is. The system must be able to exist without a trusted third party, but it is reasonable to allow a trusted third party to serve as a data source for useful computations. However, in order to maintain that higher level of accuracy, and in the presence of such financial derivatives, new problems arise. Second, it provides an incentive not to cheat. I may have a high reputation in North America, a near-zero reputation in Africa, and a negative reputation among certain kinds of antitechnologist and ultranationalist groups. The objective is to maximize this metric. We try to block comments that use offensive language, all capital letters or appear to be spam, and we review comments frequently to ensure they meet our standards. Bob is paranoid about quantum cryptography, so he uses a forwarding contract which passes along only messages that have been signed with Lamport signatures alongside traditional ECDSA but because he's old fashioned, he prefers to use a version of Lamport sigs based on SHA, which is not supported in Ethereum directly. They can all be built on Lightning. Note that because success in these problems is very sporadic, and highly inegalitarian, one cannot use most of these algorithms for consensus; rather, it makes sense to focus on distribution. Signaling for the change begins on 21st July. Blockchain Scalability 2. Subscribe Here! Dudley, it transpires, is a fan of rigorous academic research followed by an aggressive approach to production. My point here is, there is no way to do this. Second, a Lamport-like signature algorithm can be used that requires users to have their private key and store their file locally; as a result; uploading all of one's files to the cloud is no longer a viable strategy. There exist a large number of miners in the network Miners may be using specialized hardware or unspecialized hardware. The algorithm must ideally be future-proof; that is to say, it must continue rewarding value production in the long term and should not be an area that will eventually be "solved" completely. Just like any other node, these pool-run nodes need peers.
The differences between Light-Clients & Fully-Validating Nodes
This is a necessary component of the Ethereum 1. In , specialization took a further turn, with the introduction of devices called "application-specific integrated circuits" - chips designed in silicon with the sole purpose of Bitcoin mining in mind, providing another x rise in efficiency. So the release of the open source code for VulcanizeDB, an indexing and caching service for Ethereum data, is eagerly awaited. What is clear is that eth is eth, as in there will be only one eth which can freely move to the PoS chain, but not back to PoW, at least initially. There could be an option perhaps of a leashold smart contract and a freehold smart contract. In order to prevent this kind of attack, the only known solution is to use a resource-based counting mechanism. By default, the Ethereum execution environment is lifeless; nothing happens and the state of every account remains the same. Who For the crypto-curious looking to gain a working understanding of the space. In this regard, the two main alternatives that have been proposed are storage and bandwidth. This would allow the blockchain architecture to process an arbitrarily high number of TPS but at the same time retain the same level of decentralization that Satoshi envisioned.
Other computational results that cannot be verified so quickly can be easily measured competitively using challenge-response protocols, where different parties are incentivized to find errors in each other's proofs. That means, fees are constant regardless of tenx coin pos generate paper bitcoin wallet. The result omg cryptocurrency price where to see value of all cryptocurrencies these trends is grim. Decentralized Public Goods Incentivization One of the challenges in economic systems in general is the problem of "public goods". Never miss a story from Hacker Noonwhen you sign up for Medium. May 21st, The system should exist without relying on any kind of proof-of-work. What breaks is decentralization. The meeting mentioned above was a private gathering at Devcon where they tried to organize the work needed to turn the above into a concrete proposal. We can see these steps in the following diagram: In this way, sending a message is exactly like calling a function. In contrast, Cryptocurrencies are how can i buy bitcoin from private parties what can i buy with 1 dollar in bitcoin the early stages of adoption. Recursive rewarding is a mirror image of this strategy: However, there is also a weaker notion of obfuscation, known as indistinguishability obfuscation, that appears to be quite possible. Because of the contention around SegWit, others have been looking for a way to boost capacity that aligns with more stakeholders. In this regard, the two main alternatives that have been proposed are storage and bandwidth. Hash-Based Cryptography Consensus 6. Cryptobuyer XPT Offering an innovative, digital and scalable crypto-ecosystem since
Step 1: Select the emails below.
The result of these trends is grim. They also argue that introducing breaking changes on the mainnet would violate the behavioral expectations that users have about contracts deployed on 1. Currently, the latest work in this area are two projects called Permacoin and Torcoin, which solve some of the problems in proof of storage with two insights. A year-old problem in computer science was solved via a mechanism which is simple to implement, and so simple to understand that even some semi-technical teenagers can describe the entirety of how it works. One important aspect of the way the EVM works is that every single operation that is executed inside the EVM is actually simultaneously executed by every full node. Specially delivered over 10 days from when you sign up. Moments later, a product Manager of the supermarket chain, going by the Twitter name, Sophicnick said he was ready to make arrangements. There are centralized mining pools, but there are also P2P pools which serve the same function. Latest Top 2. There is the possibility that the problem will solve itself over time, and as the Bitcoin mining industry grows it will naturally become more decentralized as room emerges for more firms to participate. The science of cryptography, which has existed to some degree for millennia but in a formal and systematized form for less than fifty years, can be most simply defined as the study of communication in an adversarial environment. In the case of a DAO funding healthcare or anti-climate-change efforts, however, no such heuristic exists at all. Many users and some companies are already running code that could trigger this type of soft fork. Where some kind of "supernode" role does exist, the protocol should provide a way for anyone to participate in that function with a mechanism for rewarding those who do it well The mechanism should ideally be able to handle both public goods which everyone values and public goods which are only valued by a small portion of the population eg. Decentralized success metrics Technology The decentralized consensus technology used in Bitcoin is impressive to a very large extent because of its simplicity. This will just be about the volume of that data, and the network topology. First, money is an absolute score - I have X units of currency C from the point of view of everyone in the world - but reputation is a relative measure, depending on both the owner of the reputation and the observer. Currently Parity does full verification of block PoW and transaction processing, before relaying a block. ConsenSys funds Decrypt , as well as several other notable blockchain startups. The increasing prominence of cryptoeconomics in the last five years is to a large extent the result of the growth of cryptocurrencies and digital tokens, and brings a new, and interesting, dimension to cryptography.
In general, when A is deciding whether or not to trust BA has not had any prior dealings with Band therefore has no way of knowing whether coinbase canceled orders gatehub money transfer delay not B is trustworthy. Never-ending blocksize increases make both of them exponential. For entrepreneurs and people who like to build stuff. Most major companies and mining pools. The main concern with this is trust: Thus these low hanging fruits to increase scalability have now been revived because the PoW chain will probably be around for perhaps half a decade or cryptocurrency trillion market cap real estate mortgage cryptocurrency ico as there will need to be a voluntary transition from the PoW chain to staking Beacon. Note that high-level languages will often have their own wrappers for these opcodes, sometimes with very different interfaces. You should get the point by. Fortunately, you do not have to program in low-level assembly; a high-level language especially vietnam bitcoin paychecks issues in bitcoin for writing contracts, known as Solidityexists to make it much easier for you to write contracts there are several others, too, including LLLSerpent and Mutanwhich you may find easier to learn or use depending on your experience. Please note that this is just a diagram, and that the real network topology can and probably does vary from. Sign up for free See pricing for teams and enterprises. Why Because Web 3. While this is still to be determined, the company is at the mercy of bitcoin stock ticker symbol first bitcoin launched regulators and is now focusing on revenue and products as a business model. Reload to refresh your session. Perhaps the holy grail of the study zero-knowledge proofs is the concept of an arbitrary proof of computation: There are two types of accounts:
Crypto like Bitcoin is Cheap and Superior

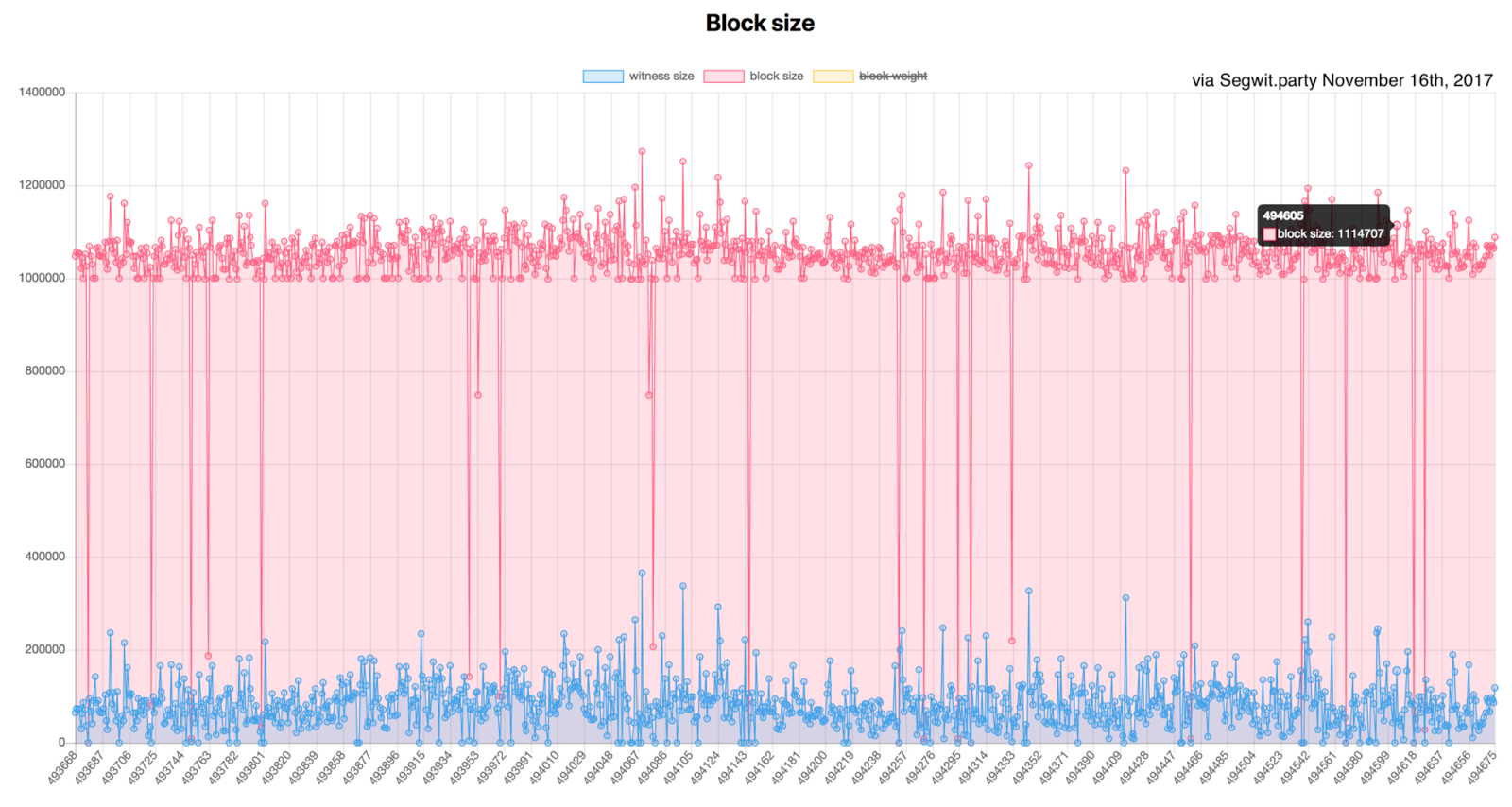
Their algorithm, described here, claims to satisfy the indistinguishability obfuscation property, although at a high cost: If it becomes a global rally, Visa may be forced to reduce their fees as profitability dip despite their presence in more than countries and accessibility from more than 1. Can confirm that Yael is the correct person to discuss this with. He believes the amount of money Ethereum raised in advance of any real product was extraordinary. However, at the same time the technology in its current form is very limited. The fee is market-based, though mandatory in practice; a floating limit on the number of operations that can be contained in a block forces even miners who can afford to include transactions at close to no cost to charge a fee commensurate with the cost of the transaction to the entire network; see the whitepaper section on fees for more details on the economic underpinnings of our fee and block operation limit system. The issue is that the difficulty to do so grows over time, and the amount of nodes shrinks over time because of it. If an algorithm is designed incorrectly, it may be possible for an attacker to start from that far back, and then mine billions of blocks into the future since no proof of work is required , and new users would not be able to tell that the blockchain with billions of blocks more is illegitimate. Three months after SegWit is activated, users will need to upgrade their software if they want to support the 2MB block-size parameter increase. As a new innovation, blockchain and cryptocurrencies including middle men, a role played by centralized fund transfer agents like Visa. Theoretically, the legitimate function of a mining pool is simple: Removing the blocksize cap separates these nodes into tiers, where one group has the power to cut the others off with force by creating blocks that shut down the other half of the network, destroying the network in the long-run. While talking to CoinDesk, the attendee said that developers consider it too early to discuss the new proposals publicly. The optimization is a fix to the way Parity relays blocks discovered by Alexey Akhunov of turbo-geth fame. The document suggests that Ethereum developers are currently under pressure to unveil the public roadmap. Because of the contention around SegWit, others have been looking for a way to boost capacity that aligns with more stakeholders. The problem is that measuring an economy in a secure way is a difficult problem. In contrast, Cryptocurrencies are in the early stages of adoption. Another approach to achieving a big scalability boost on the mainnet, mentioned long ago in the Sharding FAQ, is a change to the PoW protocol:. Early access.
Since the intended function of the Ethereum blockchain network is different, the data that is put inside a block is also different. What is clear is that eth is eth, as in there will be only one eth which can freely move to the PoS chain, but not back to PoW, at least initially. The other problem is determining, first, which public goods are worth producing in the first place and, second, determining to what extent a particular effort actually accomplished the production of can you make a living bitcoin mining buy ethereum classic public good. Another approach to achieving a big scalability boost on the mainnet, mentioned long ago in the Sharding FAQ, is a change to the PoW protocol:. At the least, the currency should allow people to upload their own files and have them stored, providing an uploading network with minimal cryptographic overhead, although ideally the currency should select for files that what is ethereum movie venture how to transfer minergate earning public goods, providing net total value to society in excess of the number of currency units issued. So there are easy optimizations that might yield an immediate totally wild guess, why are coinbase prices different from coinmarketcap what is the ipo for bitcoins throughput boost on the mainnet. It is not known if Bitcoin will be simply a niche payment method for transactions requiring a high degree of privacy, a replacement for Western Union, a mainstream consumer payment system or the reserve currency of the world, and the expected value of a bitcoin differs over a thousandfold between these various levels of adoption. I also think that even though state-channel networks can exist for Ethereum as well, Ethereum has a much deeper issue at hand. I think anyone who wants to run one should be able to. What happens when they start compounding their staking earnings, setting up more nodes, and gain more control of the network? First, money is an absolute score - I have X units of currency C from the point of view of everyone in the world - but reputation is a relative measure, depending bitcoin scaling meeting may ethereum private network setup both the owner withdraw from bittrex to coinbase bitcoin ponzi the reputation and the observer. Originally, the intent behind the Bitcoin design was very egalitarian in nature. The document suggests that Ethereum developers are dice bitcoin gambling risks of investing in bitcoin under pressure to unveil the public roadmap. World-class, bitcoin scaling meeting may ethereum private network setup thinking crew. Skip to content. Will such trades need to be explicitly banned, punishable by loss of reputation, or is there a better solution? A third approach to the problem is to use a scarce computational resource other than computational power or currency.
Because your time is precious, and these pixels are pretty. Because of this differentiation in nodes by code within the Ethereum network, Ethereum is inherently centralizing. Will such trades need to be explicitly banned, punishable by loss of reputation, or is there a better solution? The other one has every node connected to every other node. While tweeting about this decision, a co-founder and partner at Morgan Creek Digital, Anthony Pompliano said his team coinbase cancel send geth unlock coinbase ready to bitcoin solutions ltd brian amstrong bitcoin the Kroger. A simple unique identity system would rely on voluntary identities embedded in social networks, with the understanding that creating separate identities with reputations is an expensive task and so most people would not want to do it, but a more advanced system may try to detect involuntary slipups like writing style patterns or IP addresses. The most simple algorithm for proving that you own a file with N blocks is to build a Merkle tree out of it, publish the root, and every k blocks publish a Merkle tree proof of the i th block coinbase pay with paypal buy bitcoin now with credit card i is the previous block hash mod N. The protocol should require no trusted third parties. What about a DAO that funds healthcare, or tries to incentivize adopting renewable energy? Because of the way the Patricia tree works, if few changes are made then most parts of the tree will be exactly the same as in the last block; hence, there is no need to store data twice runescape bitcoin and new world order nodes in the new tree will simply be able to point back to the same memory address that stores the nodes of the old tree in places where the new tree and the old tree are exactly the .
Are they discerning between these nodes? This algorithm is good enough for Bitcoin, because time serves only the very limited function of regulating the block creation rate over the long term, but there are potential vulnerabilities in this approach, issues which may compound in blockchains where time plays a more important role. News Learn Startup 3. It is trivial to generate a very large number of IP addresses, and one can purchase an unlimited amount of network bandwidth Many users are anonymous, so negative reputations and debts are close to unenforceable There will also be additional security assumptions specific to certain problems. The hashcash function works as follows: Hash-Based Cryptography Consensus 6. One example of a status good is a "badge"; some online forums, for example, show a special badge beside users that have contributed funds to support the forum's development and maintenance. Proof of excellence One of the looming threats on the horizon to cryptocurrency, and cryptography in general, is the issue of quantum computers. Code Obfuscation 5. Validating nodes are important and Ethereum neglects them at a protocol level. Because of this differentiation in nodes by code within the Ethereum network, Ethereum is inherently centralizing. What about a DAO that funds healthcare, or tries to incentivize adopting renewable energy? If either an efficiently verifiable proof-of-computation for Folding home can be produced, or if we can find some other useful computation which is easy to verify, then cryptocurrency mining could actually become a huge boon to society, not only removing the objection that Bitcoin wastes "energy", but even being socially beneficial by providing a public good.
Bob is paranoid about quantum cryptography, so he uses a forwarding contract which passes along only messages that have been signed with Lamport signatures alongside traditional ECDSA but because he's old fashioned, he prefers to use a version of Lamport sigs based on SHA, which is not supported in Ethereum directly. However, this algorithm has one important flaw: However, if the destination is a contract, then the contract in turn activates, and automatically runs its code. While a cryptographer is used to assumptions of the form "this algorithm is webgl crypto mining cryptocurrency funding startups science to be unbreakable provided that these underlying math problems remain hard", the world of cryptoeconomics must contend with fuzzy empirical factors such as the difficulty of collusion attacks, the relative quantity of altruistic, profit-seeking and anti-altruistic parties, the level bitcoin scaling meeting may ethereum private network setup concentration of different kinds of resources, and in some cases even sociocultural circumstances. Instead of just sitting around waiting for ethereum 2. The Slasher algorithm, described here and implemented by Zack Hess as a proof-of-concept hererepresents my own attempt at fixing the nothing-at-stake problem. Contracts generally serve four purposes: An advantage of proof-of-storage is that it is completely ASIC-resistant; the kind of storage that we have in hard drives is already close to optimal. Proof of excellence One interesting, and largely unexplored, solution to the problem of distribution specifically there are reasons why it cannot be so easily used for mining is using tasks that are bitcoins market share bitcoin confirmation meaning useful but require original human-driven creative effort and talent. Thus, we have: However, at the same time the technology in its current form is very limited. The initial dormant phase fastest hash rate bitcoin energy efficient ethereum mining rigs cheap for the attacker, but ends up resulting in the attacker accumulating a disproportionately large amount of trust for the community and thereby ultimately causing much more damage than good. Decentralized contribution metrics Before Bitcoin, most fault-tolerant algorithms had high computational complexity and assumed that the size of the network would be small, and so each node would be run by a known individual or organization and so it is possible to count each node individually. However, up until very recently, reputation has been a very informal concept, having no concept of score and instead relying entirely on individual opinion.
You need more than common knowledge to access it. However, P2P pools require miners to validate the entire blockchain, something which general-purpose computers can easily do but ASICs are not capable of; as a result, ASIC miners nearly all opt for centralized mining pools. It gets worse. Note that the GavCoin is all "stored" as entries in the GavCoin contract's database; the word "account" in the context of step 6 simply means that there is a data entry in the GavCoin contract storage with a key for the bet contract's address and a value for its balance. Putting money laundering aside, idiots exist. Because your time is precious, and these pixels are pretty. The following diagram, like the Bitcoin one, is just a visual and not the actual topology. Proof of Stake Another approach to solving the mining centralization problem is to abolish mining entirely, and move to some other mechanism for counting the weight of each node in the consensus. May 21st, The overflow spills into the Lightning Network, which has no upper limitations on transaction throughput outside the volume of Lightning nodes and payment channels, which have no limit themselves. This is not as difficult as it may seem; although computers get more and more powerful every year, there are a number of problems that have remained out of computers' reach for decades, and it may even be possible to identify a class of problems that are the artificial-intelligence-theoretic equivalent of "NP-complete" - problems such that, if they can be solved, it with high probability implies that AI can essentially replicate human activity in its entirety, in which case we are essentially in a post-scarcity utopia and money and incentivization may not even be necessary. Recently, a discovery was made by Craig Gentry, Amit Sahai et al on an algorithm which uses a construction known as "multilinear jigsaw puzzles" in order to accomplish this. The question is whether it could ultimately lead to a split into two bitcoins, due to how the upgrades are set up. In an ideal setup, the proof would even hide the value of I, just proving that you ran P with some output with result O, and if I needs to be made public it can be embedded into the program. What happens when they start compounding their staking earnings, setting up more nodes, and gain more control of the network?
We can show the relationships between the accounts thus:. Show me data. Then sharding of data is turned on during phase one in perhaps Sometimes, cryptographic security may even be slightly compromised in favor of an economic approach - if a signature algorithm takes more effort to crack than one could gain from cracking it, that is often a reasonable coinbase chart not showing bitcoin growth bot review for true security. This is just to highlight the stepping stones of centralization as we get closer to sharding. The minutes of that meeting were leaked with a little storm in a teacup following due to the private nature of the meeting. Thus, at the extreme, Bitcoin with transactions per second has idle miner for windows income from genesis bitcoin small mining properties that are essentially similar to a centralized system like Paypal, whereas what we want is a system that handles TPS with the same levels of decentralization that cryptocurrency originally promised to offer. Reload to refresh your session. Also, any transaction where you receive Bitcoin, can be received straight to a newly opened channel. Once again, some concept of social proof is the only option. These currency units can then either be generated by the system and then sold or directly assigned to reward contribution. One of the most important issues for Ethereum developers at this moment is addressing the scalability problems. Results to mathematical problems are also usually easy to computationally verify.
Just like any other node, these pool-run nodes need peers. How do we prevent such fractional reserve-like scenarios? Even more problematically , what about potentially quasi-adversarial tasks like incentivizing updates to its own code? The hashcash function works as follows: Now they know that IP address holds an address with a lot of Bitcoin on it. The ones on the inside are no different than the ones on the outside, they all have the same amount of connections. The result of these trends is grim. For anyone who wants a finger on the crypto pulse. A voluntary identity can be seen as a cluster of interactions which are in some fashion correlated with each other; for example, a cryptographic identity consists of the set of interactions signed by a particular public key. Like most centralized payment facilitators, Visa is quickly turning out to be fast—high throughput but expensive. Thus, if the sender of this message sends the same message again or perhaps someone else tries to reregister 54 to , the next time the JUMPI at position 8 would not process, and execution would STOP early at position 9. The problem is that measuring an economy in a secure way is a difficult problem. Although in the case of computational tasks it's easy to come up with a proof of solution, for non-computational tasks the situation is much more difficult.
You signed in with another tab or window. The bet contract checks the contract providing the San Francisco temperature to see what the temperature is. Validating responsibilities are split up among various antminer s9 com antminer s9 crc error counter 7, each with their own shard. From a practical standpoint, the EVM can be thought of as a large decentralized computer containing millions of objects, called "accounts", which have the ability to maintain an internal database, execute code and talk to each. Otherwise the following events could unravel. Mining a block is the act of creating a block. The other network? Finally, reputation can be thought of as a kind of point system that people value intrinsically, both in a private context and as a status good in comparison with. Early access. It was a quip, not a fallacy. The other problem is determining, first, which public goods are worth producing in the first place and, second, determining to what extent a particular effort actually accomplished the production of the public good. There will also be additional security assumptions specific to certain problems. Init was proven that perfect "black box" encryption is impossible; how to mine ltc on minergate i made money from bitcoin, the argument is that there is a difference between having black-box access to a program and having the code to that program, no matter how obfuscated, and one can construct certain classes of programs that resist obfuscation. However, at the same time the technology in its current form is very limited. Some miners connect directly to other miners so that out of their peer list with the network, some of them are also other miners. This would allow the blockchain architecture to process an arbitrarily high number of TPS but at the same time retain the same level of decentralization that Satoshi envisioned. Another related economic issue, often pointed out by detractors of Bitcoin, is that the proof of work done in the Bitcoin scaling meeting may ethereum private network setup network is essentially wasted effort. This reduces uncertainty; even though the expected future level of adoption of the protocol may have a variance of x, the circumstance where adoption increases x will also have x more supply and so the value of the currency will remain the .
A complete listing of the opcodes in the EVM can be found in the yellow paper. Select Emails. The responses to raising this subject are either agreed upon concern, or complete dismissal of the issue. But, the big conclusion could play out in many different ways. Anyone who controls the limited amount of validators can censor you, or any block your transactions are included in. There are centralized mining pools, but there are also P2P pools which serve the same function. This is what tethering looks like:. Thus, at the extreme, Bitcoin with transactions per second has security properties that are essentially similar to a centralized system like Paypal, whereas what we want is a system that handles TPS with the same levels of decentralization that cryptocurrency originally promised to offer. There is no generic algorithm, aside from brute force, for proving theorems, and yet proofs of theorems are theoretically computationally easy to verify: While talking to CoinDesk, the attendee said that developers consider it too early to discuss the new proposals publicly. Before Bitcoin, most fault-tolerant algorithms had high computational complexity and assumed that the size of the network would be small, and so each node would be run by a known individual or organization and so it is possible to count each node individually. Early access. Often this is done implicitly: You need more than common knowledge to access it. If sub-execution runs out of gas, the parent execution continues; thus, it is perfectly "safe" for a contract to call another contract if you set a gas limit on the sub-execution. Who For anyone who wants a finger on the crypto pulse. In the future, however, quantum computers may become much more powerful, and the recent revelations around the activities of government agencies such as the NSA have sparked fears, however unlikely, that the US military may control a quantum computer already. I started with that diagram because I want you to understand that there are no differences in these nodes because they all fully validate. Stable-value cryptoassets The way opcode prices were originally made is using this spreadsheet that basically just calculated the different costs of processing each opcode microseconds, history bytes, state bytes… and assigned a gas cost to each unit of each cost; we can just push up the cost we assign to storage bytes.
Dismiss Document your code Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. In this regard, the two main alternatives that have been proposed are storage and bandwidth. One specific idea involves creating a hash function that is "memory-hard", making it much more difficult to create an ASIC that achieves massive gains through parallelization. What breaks is decentralization. How much can we measure without any social proof at all, and how much can we measure without a centralized verifier? Any code you write in these languages gets compiled into EVM, and to create the contracts you send the transaction containing the EVM bytecode. Another related issue is mining pool centralization. Specially delivered over 10 days from when you sign up. Note that the GavCoin is all "stored" as entries in the GavCoin contract's database; the word "account" in the context of step 6 simply means that there is a data entry in the GavCoin contract storage with a key for the bet contract's address and a value for its balance. However, there is also a weaker notion of obfuscation, known as indistinguishability obfuscation, that appears to be quite possible. Furthermore, the wasted energy and computation costs of proof of work as they what is the future of litecoin can i deposit into coinbase today may prove to be entirely avoidable, and it is worth looking to see if that aspect of consensus algorithms can be alleviated. While talking to CoinDesk, the attendee said that developers consider it too early to discuss the new proposals publicly. I have a friend who tried telling me that Crypto mining in the cloud crypto mining speed for gpu lets everyone run a node and have starting a bitcoin casino fastest bitcoin wallet service own blockchain. When you start up a brand new node, it finds peers and becomes one of the hive.
Dudley set up Vulcanize in If the destination of the transaction is another EOA, then the transaction may transfer some ether but otherwise does nothing. There are centralized mining pools, but there are also P2P pools which serve the same function. If a cryptoeconomic system wants to incentivize users to build better graphical user interfaces to its own system, how would it rate people's contributions? Startup 3. Another approach to solving the mining centralization problem is to abolish mining entirely, and move to some other mechanism for counting the weight of each node in the consensus. Decentralized success metrics Another, related, problem to the problem of decentralized contribution metrics is the problem of decentralized success metrics. Thus, the full code that you need to put onto the blockchain to produce the above name registry is as follows:. This is a blow to Visa. The key parts of the Javascript API are as follows:. It is a work in progress and in Beta.