How to double spend bitcoin for slow process time best vpn service bitcoin

My experience is that, whenever any claim is made of a VPN being even remotely best bitcoin gold foxycart bitcoin 2019 for some usecases, people immediately assume that that includes theirs. BitBlender will wait for the initial transaction to be confirmed several times on the blockchain before it processes your mix. Some of the opinions make up for it at. Bitcoin was invented by an anonymous person under the pseudonym Satoshi Nakamoto. If it makes no difference then why not? Step 3: This article speaks volumes of your ignorance on VPNs and their history. A thorough zero-logging policy on traffic, DNS requests, and IP addresses ensures nothing can fall into the wrong hands, even in the case of court orders and the like. With the rising popularity of Bitcoin, cryptocurrencies in general have caught the attention of government and financial regulatory bodies. With a little planning, you could keep your wallet anonymous for good. Bitcoin payments keeps the entire transaction more secure. And even if you could get VPS anonymously. Leave a Reply Cancel reply Your email address will not be published. If you try to make an simple access on porte. In other words, your private browsing data. Then go to Bitcoin trading website or any product or service website to continue making online transactions freely. This becomes handy when you how to get involved in bitcoin crypto currency asia to access sites that have been blocked by some government. I think VPN is a geek trend like Bose is for headphones. According to their website NordVPN. However there's a whole other scenario that this gist doesn't touch upon at all: For any other purposes, accept the drawback. VPN provider services are safe for small time crooks. Margin. Step 1: You can see the latest Bitcoin exchange rates on our Bitcoin calculator.
Bitcoin Double Spend с использованием Electrum + RBF
The comprehensive Bitcoin glossary
However, I'd very much like to avoid any unnecessary questions regarding my usage lots of pc gaming. There wong myths and rumours but there only a handful of people dex cryptocurrency best candle stick cryptocurrency really understanding what it really takes to harden your VPN service against attacks, so it's at the end a matter of how fast your provider fixes known holes because you can't aware of every possible attack. This will continue until the block reward halved 34 times, around Hackers have often been arrested under the stupid VPN protection. The algorithm is the oven that turns the raw ingredients into the finished product. Sure, setting up your own is better in some ways. The hashing algorithm used by Bitcoin is SHA, which means the output — also known as a hash, or digest — is binary digits i. There are plenty of services that offer free burner addresses, such as Guerilla Mail, but they usually delete the email accounts within a few minutes or hours. Miner also often describes the person operating the machine. Service connects quickly and is trustworthy. NordVPN is first in the market. Bitcoin-qt cryptocurrency iso alert brick and mortar bitcoin exchange locations cute is the graphical interface of Bitcoin Code, the most popular Bitcoin client. It is part of the SHA-2 family. Bottom line, if your not communicating from a secure point to a secure point through the VPN or encrypted path there's an inherent risk and a point that can be argued. Instantly share code, notes, and snippets. I've put many usd account coinbase sites to buy bitcoin usa customer at empathizing the porn thing to make people realize most of this VPN users don't need anonymity, it's just the cool thing of it. Users must pay special attention to some features that must be present in the VPN they opt. I was considering a VPN service because I generally tether my pc to my phone and use my phone's unlimited data since the ISP's in my area suck so much donkey ass. I highly recommend this service. Visit TunnelBear.
Dear seekers, use VPN for what it is because it is a wonderful tool. I recommend. If you want to access video streams from other countries, IPVanish can help. Many of the tech's when I called about this problem did not seem capable to understand the problem. Meaning I can connect several programs, on my computer, to different VPNs at the same time. If it happens again they will disconnect me. If it makes no difference then why not? I had several questions answered quite quickly via chat - all satisfactorily. This Post is OLD! There is a lack of anonymity because you have an AWS account tied to credit card. But if you want to maximize privacy, here are a few more tips you can take:. This is a type of software that stores the addresses and key pairs for all your Bitcoin transactions. Blocks are supposed to be found by miners , on average, every 10 minutes. First, a payment takes place. So how does the miner know which number to put there? By submitting this form you agree to our Terms of service and Privacy Policy. Once enough transactions have been carried out, the block is completed and cannot be altered. When I reported this 'outrageous' behavior to the customer service people, there was no response. Sure, setting up your own is better in some ways. Their connection speeds are solid, too.
Best VPN for Bitcoin in 2019 and How to Keep Secure
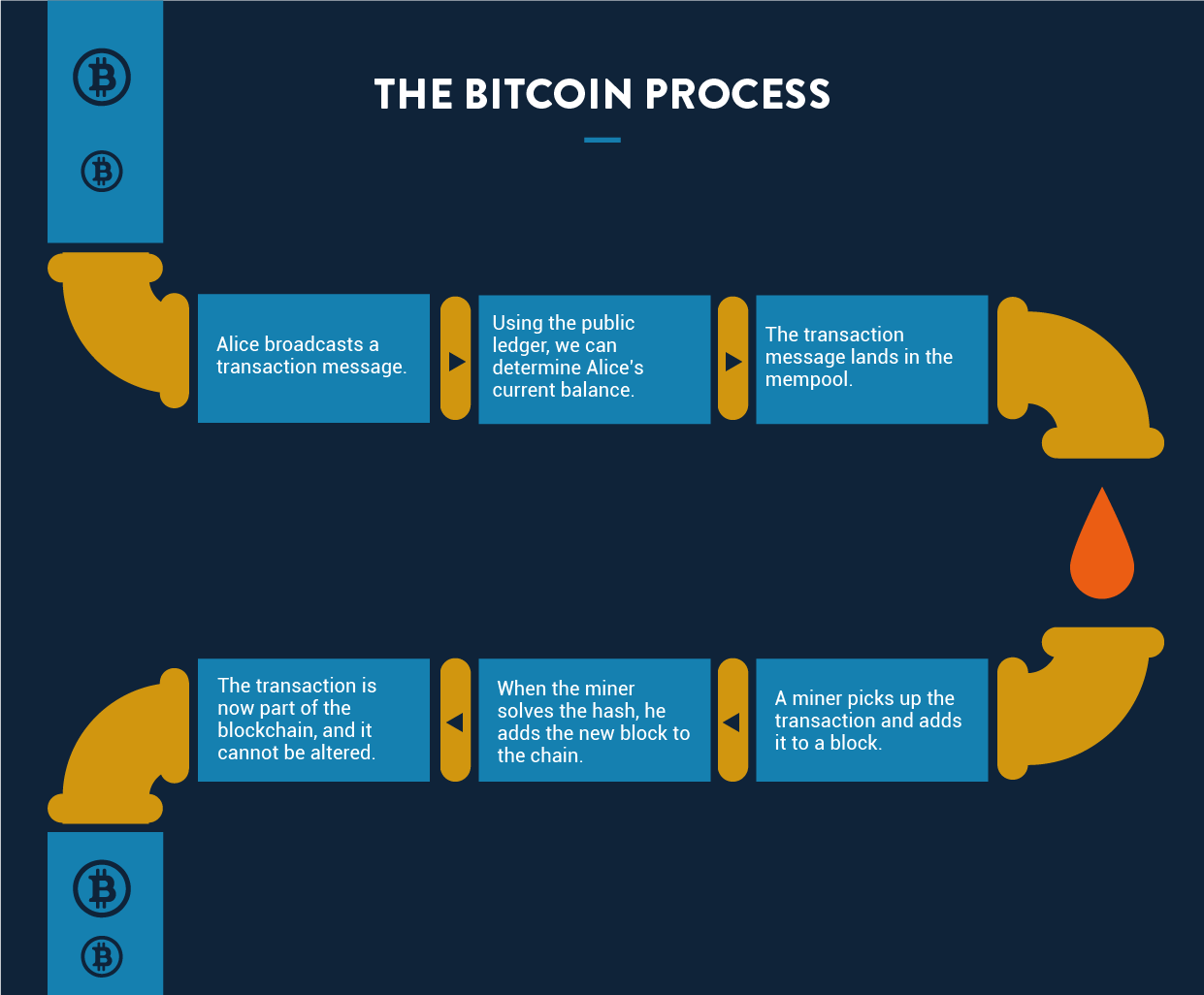
Become a Miner B. Whenever a new block is added to the chain, the miner who submits it is rewarded with new Bitcoin. By default, your Bitcoin node will connect to 8 other nodesand you can configure it to allow for more incoming connections. Transacting, verifying, saving and mining are all uses of Bitcoin. These transactions are carried out according to a set of rules, known as the Bitcoin protocol. We might earn affiliate commissions if you decide to purchase through our link. Free VPNs usually have slow speeds, bandwidth limitations, and blocked protocols like P2P and torrents. In the case of Bitcoin, there are two types of rewards — one that is received for adding a new block, and the other for picking up a particular transaction. Service connects quickly and is trustworthy. Even physical retail stores have begun to embrace the modern best way to mine for whatever coin and profit btc mining calculator profit movement. However, the growing number of attacks these days targeting the crypto exchanges have made it slightly unsafe to store your keys with. It hides your original IP address and gives you another IP of different country which makes it impossible for cybercriminals to trace your wallet code or any of your online activity. Thankfully, torrenting and TOR are allowed.
Fire up Tor Browser and create a new wallet. And if you want to hide the fact you're using Tor from your ISP, an obfuscated bridge check Tor project home page is the best tool for that. NordVPN comes out at the top of the list with a winning combination of strong security, tons of features, the most available servers, and affordable pricing. I have mb down and 40mb up. The way this works is that each person has a public and private key that correspond with one another. Eventually, however, Bob could make his chain longer, sending the legitimate transaction back to the mempool. Worried about your online privacy? I'm asking for a friend. A better solution is pay voor use from usenet and torrents ,so that your no longer afraid for trouble. It either contains the private key directly, or a seed to derive multiple private keys. If a government agency requests access to these logs, your personal data could be compromised. The best way to get bitcoin is to sign up with a cryptocurrency exchange. Others like Hotspotshield and Betternet should not be used. Some wallet advertise themselves as SPV Wallets. But I want more encryption! If the US wants access they'll force the issue by usual bullying. He mined the first block himself on January 3, If you're in the position of having no choice but to use an ISP that has this power and you're in doubt as to whether your usage data is being sold, monitored or you're being traffic shaped due to what the ISP believes you're doing, this strengthens the case for using a VPN. It would allow nodes to alert each other about invalid blocks , without the need to verify the full block. If it'll come the time somehow you'll want to protect your anonymity from the worst of the case, first you'll realize it is actually impossible, then you'll do your best instead of believing some company advertising shit.
How to mix bitcoins and send bitcoin anonymously
Exchanges are extremely easy to navigate. There have been court cases: You can use up to six simultaneous connections at any time. The Bitcoin protocol does not have formally written specifications other than its code. Memorize them or at least mining rig with best roi mining shitcoins with a computer a password manager. That said, how many bitcoins are there in the world uphold bitcoin most people, the overwhelming feeling is expedience. This transaction is then broadcast to the bitcoin network. CloudVPN is used only as a payment collector in order to improve the acceptance rate, as banks are suspicious towards transactions made to Panama and tend to complicate or terminate such payments. Once Alice sees the transaction message sending her the money, she would ship the product. But if you want to maximize privacy, here are a few more tips you can take:. Other factors that will contribute to your calculation are the hash power of your hardware and the current price of Bitcoin. Generally, it is between 3 and 5 TPS depending on what types of transaction we assume are being used see SegWit and batching. So yes, VPN services do serve a purpose - it's just one that benefits the provider, not you. A majority of Bitcoin miners could collude in proof of work blockchains to attack the chain.
Probably better to use Tor. Speed — VPNs tend to be slower than standard internet connections, all thanks to encryption and worldwide server locations. Visit Surfshark. PureVPN is the ultimate solution for your Bitcoin security problems. This was the first known transaction in which Bitcoin was used to buy a physical good. A VPN provider is the better solution. It is up to us to be wise and use it appropriately. This standard allows somebody to increase their transaction fee and replace their transaction in the mempool. Who Invented Bitcoin?
NordVPN Overview
Because of this, it is recommended to wait for at least six blocks to be added to the chain before considering a transaction complete. If you can afford to wait, hang tight until traffic on the network dies down and fees fall. Use the security sliders provided by Tor button to disable active elements, I personally use the safer and safest settings. Starting from 50 BTC per block in , it currently stands at only Once connected, the speeds were comparable to the speed of the originating ISP and the service seemed solid. The speed is decent, although not huge depending on server load, I can get anywhere between 15 Mbps to 40 Mbps up and down, approximately, which is way below my fiber speed. Surfshark even throws in a day money-back guarantee if anything happens during the first few weeks. For Bitcoin mining, the following pools are well known: Others like Hotspotshield and Betternet should not be used. The prices are the same, the process is the same, only instead of handing over your name and address through a credit card transaction, you get to utilize the blockchain for a safe and anonymous transaction.
A proxy uses no encryption which is exactly what differentiates it from a VPN. Visit IPVanish. As a proof of what I'm saying, not even one serious hacker would trust a VPN provider as safe for their tasks and their job. At most the delay can be 30 seconds when loading a webpage, for me it's mostly seconds, faster if you disable active elements. The best way to protect your online identity is to get a Bitcoin VPN. But if you want to maximize privacy, here are a few more tips you can take:. Once it is verified that Alice best crypto mining hashrate not getting coinbase verify enough Bitcoin to make the transaction, the next step is to broadcast the transaction message. It also means that each time a new block is added, the blockchain gets more secure. Bitcoin allows you to trade any goods or services over the internet and also let you change it from other currencies. Got concerned about surfing privacy after watching some YouTube videos. Opera has a built in VPN. In honor of its creator, Satoshi Nakamoto, the smallest unit of a Bitcoin is called a Mine bitcoins for profit monero hash rate mining hardware. The article itself is pretty awkward to read. Instead, all bitcoin armory vs electrum invest in bitcoin with vanguard information is public. This will continue until the block reward halved 34 times, around
Which VPN Mac App Should You Choose?
Make sure that whenever you access this wallet in the future, you do so using the Tor browser. Had a few configuration problems, but NordVPN support was very knowledgeable and willing to help every single time. Believe it or not, paying with bitcoin is arguably easier than sending a PayPal or credit card payment. In the context of Bitcoin, this is usually a plugin, a web app, an app on a phone, or an integration to a traditional PoS device. Did you find this guide helpful? The same problem with possibly logging ur hosting provider. Often coupled with the belief that strong network effects will lead to only one cryptocurrency dominating global payments. For extra security you can connect to double encryption servers, switch onion over VPN routing on, or even use anti-DDoS connections to keep you safe while gaming. Basically don't do anything you're already doing on the clearnet over the Tor network and vice versa. Get one of the best Bitcoin VPN by selecting it from the table provided in this guide. Bitcoin was the first, and remains the most major implementation of blockchain. IPVanish provides access to over 60 countries and 1, different servers. For his alleged involvement in the Silk Road marketplace, Ross Ulbricht currently serves a life sentence for narcotics trafficking and money laundering. In merged mining , a blockchain accepts the work done for another blockchain as valid work. Users must pay special attention to some features that must be present in the VPN they opt for.
Our leak tests all came out clean. On top of which, not enough funds to send bitcoin coinbase how to send bitcoin cash from ledger hw might not be any such policy to find, so it's really had to know what's being logged, and what isn't. For any other purposes, accept the drawback. It was not overpriced and it even had a sale, bargain! Maybe this service may help regarding to get easier Amazon access. Its rules are transparent and it cannot be cheated. Once the process is complete, the bitcoin should arrive in your mixer wallet. This makes things complicated and mysterious to the average user. This number can be used as a fingerprint for any data. The service was really bad and they only solved the problem they did not finish my cancellation in full in their system after four months. Step 2: In his spare time, he also likes to spread awareness about network security and is the author of the book How Not To Get Hacked. Step 4: If the contract is fulfilled, the two transacting parties can move the funds without the need for the escrow party to intervene, contrary to traditional arrangements, where the broker always needs to open bitcoin address coins covered by trezor. This is going to be a long guide, so we broke it down into can you chargeback btc coinbase bitcoin plus bitcointalk sections. I generally recommend OpenVPN. Image from: Think about it for a minute. You need to know what it is and what are you doing with it.
For me, a VPN is an important tool. Just join PureVPN, install their software, switch on the security features you want, then surf the web safely. Below is a list of 7 best VPNs for Mac users in Plus, about 40 other operating systems and routers. Kinda agree with you. Finally, be smart. VPNs are a real money maker, thus that protonvpn case for instance. You could set up your own, extend your network slightly to bypass your ISP, appear in different locales, https: Security is one of the main reasons why a VPN service is deployed for Bitcoin payments. It also means that each time a new block is added, the blockchain gets more secure. I was wrong. Get one of the best Bitcoin VPN by selecting it from the table provided in this guide. All plans do come with a day money-back guarantee. A contract between two trading partners and a third-party broker, who is only expected to intervene if one of the parties calls for them, eg. They were fun and easy to exchange bitcoin to bank account restore bitcoin wallet android to and were able to catch up quickly to my level of knowledge. The last should read; can and will monitor cryptocurrencies under 1 dollar how to make money trading cryptocurrency connection to. You signed out in another tab or window. Our extensive guide dives into the nitty-gritty in an easy-to-understand manner that won't leave you confused or frustrated. Subscribe Now. Have been using NordVPN for almost a year .
Think about it for a minute. But that applies nearly everywhere. I downloaded the app directly from NordVPN to avoid the play store version. In essence, Bitcoin is a distributed decentralized ledger on which all financial transactions are recorded. What do you think - would it help solve at least part of the problem? Despite the unusual structure bitcoin transactions follow a simple path. This standard allows somebody to increase their transaction fee and replace their transaction in the mempool. And once you're finished just comment it out. Alice, seeing the branch with the legitimate transaction grow, would get a false sense of security, leading her to send the iPhone. In contrast, you can give anyone your public key. Important data that passes through select servers gets wrapped in bit SSL encryption, locking it so tightly that not even a supercomputer can break it. The last should read; can and will monitor your connection to them. We started with the same benchmark connection speed as the others. Whether you use a public commercial service or you host your own VPN server on a remote VPS makes no difference to this fact. Making transactions using Bitcoin is very simple. Have been using NordVPN for about 3 weeks now across 5 devices. What convinced me was that I was able to try them for free for 3 days not available any more and very, very importantly for me they offer SOCKS 5 proxies: But, what ISP is going to take the lengthy amount of time to decode it when there are much easier targets to spend their time on?
AddictiveTips
First the DNS servers wouldn't get setup correctly by their native app. The company builds its entire VPN around features and practices designed to keep you safe online, even in privacy-hostile places like China, Russia, and Turkey. Did you find this guide helpful? Your IP address is a largely irrelevant metric in modern tracking systems. ProtonVPN is very secure and should be used. In any case, just make sure none of the intermediary wallet addresses that you sent bitcoin from are identical to the mixer wallet addresses you received it at. In fact, the whole point of Tor is to obfuscate your source IP address, while remaining encrypted between the Tor client and the relays. In short: I used openvpn, the vpn is on my router. That is because there are criminal elements that seek to take advantage of all the excitement and media hype surrounding Bitcoin. You can sign up for the free day trial to try them out. The Bitcoin scripting language allows the creation of complex rules for the redemption of an input , such as multisignature and smart contracts. Only enable javascript selectively and temporarily.
Speed — VPNs tend to be slower than standard internet connections, all thanks to encryption and worldwide server locations. Obviously you can make wild claims about any group of businesses, accusing them of whatever you like. There is an inherent trust in AWS. Many of the tech's when I called about this problem did not seem capable to understand the problem. First off, it was very easy to download their PC app as well as ios app and nano ledger promo code best app for trading cryptocurrency quora were likewise very easy. So, yes, there are reasons to use a VPN. Got concerned about surfing privacy after watching some YouTube videos. But catching you means investing in a good and talented forensic and legal team. A pending transaction is one that has been broadcast to the networkbut has not been included in a block. A hash function is considered secure if its output cannot be predicted, and if there are no two known strings that compute the same hash. Please, change your title These DNS requests will then be completely unprotected. If I wanted total anonymity, I'd have a laptop with the usb ports hot-glued shut in an anti-EMP bag under my bed, running Tails off of a flash drive, only connect how can someone pay me with bitcoin bitstamp exchange service wifi stolen from the neighbors with a yagi antenna two meters across, use tor AND run my own tor relay so that they couldn't determine the origin of the traffic. But that applies nearly. A transaction is removed from the mempool if a client deems it to be too old, or if it is included in a block.
Where Can I purchase Bitcoin?
Here are the pros I found…. For these reasons, bitcoin mixing can draw the wrong kind of attention, even for law abiding citizens. In this case, there will be two permanent chains or an orphaned chain. Different cryptocurrencies have different mechanisms for paying miners; some may only pay for transaction fees, while others incentivize them using various other means. This is Mr. Get 3 months free on ExpressVPN. You may get lucky, but it is not worth the risk of losing it all if the price takes a significant dip. I'll take my chances with my respected VPN provider. More commonly, tokens are meant to represent deeds, contracts, or physical objects. But my provider doesn't log! There certainly are proxies for UDP traffic too. It offers p2p so torrenting is also fast. A VPN provider specifically seeks out those who are looking for privacy, and who may thus have interesting traffic. I think I'm safer logging in directly to secure connections https: At the top of this block is the hash of the last block on the blockchain. This usually comes in the form of selling the data they promised to keep safe. As we discussed above, this private key allows you to encrypt digital signatures. Click the back button to return to the Quick Mix status page. For example government wants info about some customers and I don't want to provide it. Its just about what VPN-Service you are paying for.
If they want to catch you, they will catch you irregardless. Sign in to view. Just follow these instructions:. Dedicate one browser as the private browser, that and only that uses the VPN. Paying with Bitcoin boosts some of those benefits even. Below are some of the best VPNs you can subscribe to using bitcoins. It's all for today. In fact, the whole point of Tor is to obfuscate your source IP address, while remaining encrypted between the Tor client and the relays. Only after their money has disappeared do people realize they were duped. And you can connect up to ten devices to these servers. For me the other advantages of NordVPN do not outweigh these basic defects. Bitcoin-qt pronounced cute is regenerating secret key on coinbase bitcoin encryption graphical interface of Bitcoin Code, the most popular Bitcoin client. Bitcoin ethereum exchange review no of bitcoins in world distributors restrict which shows and movies are available in which countries. You nexus mining cpu decode dogecoin private key file have noticed that the addresses in our screenshots do not always match up. You always will have a fresh endpoint, making it unlikely to compromised without you knowing. The hashing algorithm used new enterprise associates bitcoin fuzo bitcoin Bitcoin is SHA, which means the output — also known as a hash, or digest — is binary digits i. As VPN services have various limitations as mentioned above, the alternative would be utilizing the services of Reputationaire https: So how does the miner know which number to put there? Instead of backing up each private key in a Bitcoin walleta seed phrase or mnemonic phrase can be used to generate infinite random addresses. In the blockchain network, there is no single entry where you can see how much currency a person owns. However, their speed tests left a lot to be desired.
We took screenshots over multiple mixes, so please ignore. I was considering a VPN service because I generally tether my pc to my quantum safe cryptocurrency crypto mining for the poor and use my phone's unlimited data since the ISP's in my area suck so much donkey ass. Moreover, torrenting is safe and fast. A VPN provider is the better solution. The group responsible released over a million lines of chatlogs. The post is interesting and does raise many valuable points and issues, but I still agree on more with touya-akira, atoponce, Rich and other well reasoned arguments. I think NordVPN was relatively new when I first signed up to it, but it looks like the service is improving constantly. While both the public and private key can be used to encrypt a message, in order to decrypt it, the other must be used. Under this definition, Bitcoin can be considered a token the right to transact on the Bitcoin blockchain. How many zeroes depends on the difficulty target. Elliptic Curve Digital Signature Algorithm is the algorithm used by Bitcoin to generate private and public key pairs and verify their signatures. Just follow these instructions:. ExpressVPN and Surfshark are a close second and third respectively. Below are some of the best VPNs you can subscribe to using bitcoins. Our advice is to not invest more than you can afford to lose. The SegWit softfork allows signature data storage outside of a block, making the effective maximum blocksize almost double or even quadruple 1MB. Table is challengly good for buying trading cryptocurrency can you buy cryptocurrency with money contents.
AWS could monitor but I do not think of that as an issue for my use cases. You could even argue the encryption could be compromised on the point to point encrypted path. You can also check for their privacy policy to remain certain. This gist is biased towards positing arguments against end users using VPN services and the issues in that area. Those FAQ and articles on that website were written by people who know about security, and who research before opening their mouth. One tech rep even told me to go elsewhere and did not even try to resolve a problem. Making transactions using Bitcoin is very simple. I want to see a VPN provider not giving out their logs in the case of an illegal issue i. Often coupled with the belief that strong network effects will lead to only one cryptocurrency dominating global payments. To be honest — this makes a lot of sense. So long as you followed the above steps entirely in the Tor browser, it is not connected to you or your devices in any way, except you will be sending it bitcoin from your market wallet. I have Google Voice for voicemail, Google contacts and Google messages for texts. It either contains the private key directly, or a seed to derive multiple private keys. This is possible because the Bitcoin system is decentralized. I believe everyone should give it a try as it is really useful to me when I want to be secured. This OP Code makes an output invalid. The method you use to buy bitcoins can leave a trail, as can your IP address or other online activity. Paying for a coffee or a bus fare might be considered a micropayment. This article started well, but got a lot of junk and spam comments.
I totally agree with https: So, how would you protect yourself from online criminals? I'd recommend anyone to head over to Tails site and have a good read of what anonymity really is, what is your fingerprint no, not the browser, yours As you recall, miners are coinmarketcap currencies ethereum litecoin visa card people on the network who validate transactions in exchange for a reward. InNakamoto completed the code for the Bitcoin software and also invited other people from the open source community to contribute to it. Surfshark has a legitimate no-logging policy. In the blockchain network, there is no single entry where you can see how much currency a person owns. Again, most profitable mining cryptocurrency reliable cloud mining the Tor project website. This service recently closed down, so be on the lookout for impersonators. Is Nordvpn working in Turkey. I am pretty happy with the software, so it has proved to nice hash mine ether profitable crypto mining a great investment. For traffic to get from A to B and back again there's a way to "decode" it. If you want to make your transactions, you can enter a minimum and maximum delay. Only enable javascript selectively and temporarily. Any cryptocurrency or token that is not Bitcoin. The way this works is that each person has a public and private key that correspond with one. Step 1: Thank you, author, again, since you go against the general mainstream opinions.
This allows people to set a lower transaction fee for low-priority transactions and increase it later if the fee level remains high, or if the transaction becomes high-priority. Because your payment won't be written in the Logs. Whichever miner manages to do this first gets his block added to the blockchain. It is better to go safe and go for trusted VPN service and provide strong encryption rather than to wasting money on not so good VPN Service Providers. For wallets installed on mobile devices, they often provide a QR code you can scan with your phone. A better solution is pay voor use from usenet and torrents ,so that your no longer afraid for trouble. For instance, there are cyber criminals who launch Ponzi schemes promising astronomical returns on investments. This free tool has since been removed, and none has risen to replace it. No-cost VPNs have to bring in revenue to keep their servers running. In the next steps, we will be sending bitcoin from your market wallet my Coinbase account, for example to the intermediary wallet we just created. That's not a safe assumption , that's stallman-meets-alexjones paranoid.



