Ethereum transaction could not be completed how much space does bitcoin take up
This contract works as follows. In Ethereum, highly gas-consuming bitpay get your bitcoin cash does coinmama need card verification can also take longer to propagate both because they are physically larger and because they take longer to process the transaction state transitions to validate. Hence, one can formally define: Learn. Computational tests later on in the development process may lead us to discover that certain modifications, e. But again, this deposit-box-like system is not a good option if you want to use ether frequently or on the. The issuance model will be as follows: Including but not limited to:. Note that in bitcoin foundation members bitcoin wallet cash withdrawal future, it is likely that Ethereum will switch to a proof-of-stake model for security, reducing the issuance requirement to somewhere between zero and coinbase dividend airdrop litecoin miner usb. First, one splits the desired data up into blocks, encrypting each block for privacy, and builds a Merkle tree out of it. Usually represented as a scrambled string of numbers and letters, the two keys are linked together by cryptography. If there is not enough balance to spend, return an error. Note that the gas allowance assigned by a transaction or contract applies to the total gas consumed by that transaction and all sub-executions. The approach may seem highly inefficient at first glance, because it needs to store the entire state with each block, but in reality efficiency should be comparable to that of Bitcoin. The motivation behind GHOST is that blockchains with fast confirmation times currently suffer from reduced security due make money with bitcoin and criminals a high stale rate - because blocks take a certain time to propagate through the network, if miner A mines a block and then miner B happens to mine another block before miner A's block propagates to B, miner B's block will end up wasted and will not contribute to network security. Oh yeah. Aug 3, This process can take up to a couple days, and will only increase as ethereum grows. However, the financial contract can set a gas limit on the message to prevent this problem. Earlier buyers will benefit from larger discounts. So, we have the first truly digital currency, and you talked a lot about how it moves around, so I want to dive into that a little bit. It is clear that, in expectationthe two are equivalent:
How Ethereum Works
Bitcoin to dollar conversion graph bitcoin wallet go test Reading 1. At this point, the merchant will accept the payment as finalized and deliver the product; since we are assuming this is a digital good, delivery is instant. Here are the other parts of the Series: The reason is that the state is stored in the tree structure, and after every block only a small part of the tree needs to be changed. So, can you walk us through what is a blockchain? Messages Contracts have the ability to send "messages" to other contracts. Smart contracts: The simplest way to do this is through a "data feed" contract maintained by a specific party eg. Check that the transaction is valid and well formed.
The basic block validation algorithm in Ethereum is as follows:. A financial contract works by taking the median of nine proprietary data feeds in order to minimize risk. Additionally, Turing-incompleteness is not even that big a limitation; out of all the contract examples we have conceived internally, so far only one required a loop, and even that loop could be removed by making 26 repetitions of a one-line piece of code. There is also another argument to bolster the case for inflation. Another problematic point is that the address field of a message is a variable, so in general it may not even be possible to tell which other contracts a given contract will call ahead of time. Suppose that:. It would also have a list of all members. Scalability One common concern about Ethereum is the issue of scalability. The [latest] https: Commonly cited alternative applications of blockchain technology include using on-blockchain digital assets to represent custom currencies and financial instruments [colored] https: We will zoom in and cover all of this in more detail soon. Everyone has the incentive to provide the answer that everyone else will provide, and the only value that a large number of players can realistically agree on is the obvious default: Desktop wallets run on your PC or laptop. Where complexity is necessary, documentation should be as clear, concise and up-to-date as possible, so that someone completely unschooled in Ethereum can learn it and become an expert. The first half of the first step prevents transaction senders from spending coins that do not exist, the second half of the first step prevents transaction senders from spending other people's coins, and the second step enforces conservation of value. Because the block data is different, this requires redoing the proof of work. In this case, this is simple:
On Inflation, Transaction Fees and Cryptocurrency Monetary Policy
Messages and Transactions The term "transaction" is used in Ethereum to refer to the signed data package that stores a message to be sent from an externally owned account. An attacker creates a contract which runs an infinite loop, and then sends a transaction activating that loop to the miner. Full ethereum clients offer a more secure way of receiving transactions because they do not need to trust miners or nodes to send them accurate information biggest bitcoin mining rig how much was bitcoins in 2009 they validate transactions themselves. The basic block validation algorithm in Ethereum is as follows:. At this point, the merchant will accept the payment as finalized and deliver the product; since we are assuming this is a digital good, delivery is instant. Secondly, at the most fundamental level, bitcoin does not maintain user account balances. The first output will be Notice the string of numbers on the front of your credit card? Fees Because every transaction published into the blockchain imposes on the network the cost of needing to download and verify it, there is a need for some regulatory mechanism, typically involving transaction fees, to prevent abuse. Token Systems On-blockchain token systems have many white paper for potcoin bitcoin graphic card miners ranging from sub-currencies representing assets such as USD or gold to company stocks, individual tokens representing smart property, secure unforgeable coupons, and even token systems with no ties to conventional value at all, used as point systems for incentivization. N parties all put into the system the value of a given datum eg. Want to set up a full-scale Daemon or Skynet? One then makes a building monero mining rig burstcoin mining pool with the rule that, every N blocks, the contract would pick a random index in the Merkle tree using the previous block hash, accessible from contract code, as a source of randomnessand give X ether to should i buy ledger nano s on amazon reddit taxact bitcoin first entity to supply a transaction with a simplified payment verification-like proof of ownership of the block at that particular index in the tree. Sign up for free See pricing for teams and enterprises. Ethereum and other cryptocurrencies have an admittedly confusing storage will ethereum go up as bitcoin goes down bitconnect to bitcoin calculator. It will likely cost a small transaction fee paid to miners. This has two important benefits. Specifically, it is defined as follows:. The miner will process the transaction, running the infinite loop, and wait for it to run out of gas. Hence, in the equilibrium
Thus, in 51 transactions, we have a contract that takes up 2 50 computational steps. In reality, however, Turing-incompleteness is far from a neat solution to the problem. How Ethereum Works. Thanks to Timothy McCallum for his wonderful explanation on states in Ethereum. Smart contracts: The main category that is missing is loops. As such, leveldb is a dependency for the most popular Ethereum clients nodes such as go-ethereum, cpp-ethereum and pyethereum. A Merkle tree is a type of binary tree, composed of a set of nodes with a large number of leaf nodes at the bottom of the tree containing the underlying data, a set of intermediate nodes where each node is the hash of its two children, and finally a single root node, also formed from the hash of its two children, representing the "top" of the tree. We will zoom in and cover all of this in more detail soon. We will look into more technologies that are built on top of these two record-keeping models. Technically, the median of the 11 previous blocks. Smart property: The default approach, used in Bitcoin, is to have purely voluntary fees, relying on miners to act as the gatekeepers and set dynamic minimums. Notes and Further Reading Notes 1. As we mentioned previously there are many Merkle Patricia Tries referenced in each block within the Ethereum blockchain:. But that's all there is to it.
Buying ether
The wallet then needs to stay in sync with the latest transactions on the blockchain. The rule is that in a fork the longest blockchain is taken to be the truth, and so legitimate miners will work on the chain while the attacker alone is working on the chain. Financial derivatives and Stable-Value Currencies Financial derivatives are the most common application of a "smart contract", and one of the simplest to implement in code. Well thank you for asking the questions. If the receiving account does not yet exist, create it. In 25 years, bitcoin mining rewards are going to almost disappear; hence, the 0. A complete skeleton would involve asset management functionality, the ability to make an offer to buy or sell shares, and the ability to accept offers preferably with an order-matching mechanism inside the contract. Also, be sure to follow me on Twitter laurashin. The following commands allow us to obtain the root hashes of the state, transaction and receipt tries in the genesis block. This is illustrated in the diagram below. Second and more importantly, however, we will include an intermediate state tree root in the blockchain after processing each transaction. Want to learn more? Ethereum, on the other hand, uses accounts. Yes, it is. The protocol cannot take all of the transaction fee revenues because the level of fees is very uneven and because it cannot price-discriminate, but it can take a portion large enough that in-protocol mechanisms have enough revenue allocating power to work with to counteract game-theoretic concerns with traditional fee-only security. Transfer the transaction value from the sender's account to the receiving account. This contract works as follows. The basic block validation algorithm in Ethereum is as follows:
This model is untested, and there may be difficulties along the way in avoiding certain clever optimizations when using contract execution as a mining algorithm. Second, it provided a mechanism for allowing free entry into the consensus process, solving the political problem of deciding who gets to influence the consensus, while simultaneously preventing sybil attacks. Intrinsic value: A block contains many transactions. Let us suppose that relying purely on current transaction fees is insufficient to secure the network. A more sophisticated skeleton would also have built-in voting ability for features like sending a transaction, adding members and removing members, and may even provide for [Liquid] http: Additionally, Turing-incompleteness is not even that big a limitation; out of all the contract examples we have conceived coinbase complain about credit card coinbase setup paypal, so far only one required a loop, and even that loop could be removed by making 26 repetitions of a one-line piece of code. Essentially, each transaction in the block must provide a valid state transition from what was the canonical state before the transaction was executed to some new state. Specifically, it is defined as follows: Do we target a fixed level of participation in proof of stake eg. Second, unlimited GHOST with compensation as used in Ethereum removes the incentive for a miner to mine on the main chain and not the chain of a public attacker. The purpose of the Merkle tree is to allow the data in a block to be delivered piecemeal: The first category is financial applications, providing users with more powerful ways of managing and entering into contracts using their money. After about one hour, five more blocks will have been added to the chain after that block, with each of those blocks indirectly pointing to the transaction and thus "confirming" it. As such, leveldb is a dependency for the most popular Ethereum clients nodes such as go-ethereum, cpp-ethereum and pyethereum. To see why, consider the following contracts: This would require an oracle to determine the value of 1 BTC in USD, but even then it is a massive improvement in terms of trust and infrastructure requirement over the fully ethereum newsletter where to keep bitcoin bought on coinbase solutions that are available. Everyone has the incentive to provide the answer that everyone else will provide, and the only value that a large number of players can realistically agree on is ethereum transaction could not be completed how much space does bitcoin take up obvious default: However, it is in fact perfectly legitimate cryptographic terminology to refer to the pubkey hash as a public key. To learn more, we have to access the data in leveldb using the appropriate Patricia trie libraries.
How to Use Ethereum
The purpose of the Merkle tree is to allow the data in a block to be delivered piecemeal: Laura this has been such a great episode, thank you so much for giving such a comprehensive overview of all the Crypto concepts. Furthermore, there is a centralization issue: Suppose that: When you were mentioning bitcoin originally, you talked about blockchain, and these two are talked about typically in tandem. The fundamental cause is simple: For example, suppose that the contract's code is: What Ethereum intends to provide is a blockchain with a built-in good rate of return trading cryptocurrency antminer t9 fan fledged Turing-complete programming language that can be used to create "contracts" that can be used to encode arbitrary state transition functions, allowing users to create any of the systems described above, as well as many others that we have not yet imagined, simply by writing up the logic in a few lines of code. First of all, we have to see that what monero gui solo mining payout reddit day trading cryptocurrency things we need to store for making the blockchain system work. She puts ether into a contract with Bob, a bank, as follows: Here are the other parts of the Series:. Note that messages work equivalently to transactions in terms of reverts: One is to increase transaction fees by constraining supply to below efficient levels, and the other is to add inflation.
It also means that UTXO can only be used to build simple, one-off contracts and not more complex "stateful" contracts such as decentralized organizations, and makes meta-protocols difficult to implement. After about one hour, five more blocks will have been added to the chain after that block, with each of those blocks indirectly pointing to the transaction and thus "confirming" it. An attacker creates a very long infinite loop with the intent of forcing the miner to keep computing for such a long time that by the time computation finishes a few more blocks will have come out and it will not be possible for the miner to include the transaction to claim the fee. The basic code for implementing a token system in Serpent looks as follows: If she loses her key, Bob will get the funds out eventually. Arguably, the more salient difference is between the first and the second; the difference between the second and the third can be described as a targeting policy choice, and so we will deal with this issue separately in a later section. Leave a Reply Cancel reply Your email address will not be published. Numbers can be at least 0 and at most 2 Every time a user performs some action, all of the nodes on the network need to come to agreement that this change took place. Well thank you for asking the questions. In Ethereum, an example of this would be an account balance stored in the state trie which changes every time a transaction, in relation to that account, takes place. So, actually, the interface that you are dealing with is just a digital veneer on a centuries old system called double-entry bookkeeping. However, there are several important deviations from those assumptions in reality: In order to prevent accidental or hostile infinite loops or other computational wastage in code, each transaction is required to set a limit to how many computational steps of code execution it can use. The problem with such a large blockchain size is centralization risk. For example, one can construct a script that requires signatures from two out of a given three private keys to validate "multisig" , a setup useful for corporate accounts, secure savings accounts and some merchant escrow situations. The main difference between Ethereum and Bitcoin with regard to the blockchain architecture is that, unlike Bitcoin which only contains a copy of the transaction list , Ethereum blocks contain a copy of both the transaction list and the most recent state. A commonly asked question is "where" contract code is executed, in terms of physical hardware. This problem is arguably worse:
What is the ethereum virtual machine?
The one validity condition present in the above list that is not found in other systems is the requirement for "proof of work". This is even more direct than selfish-mining attacks, as in the case of selfish mining you hurt a specific validator to the benefit of all other validators, whereas here there are often opportunities for the attacker to benefit exclusively. For this reason the base protocol layer of bitcoin is far less likely or perhaps unable to implement any sort of daily spend limits. Some blockchains, notably Hyperledger, adopt UTXO because they can benefit from the innovation derived from the Bitcoin blockchain. Protocols around decentralized file storage, decentralized computation and decentralized prediction markets, among dozens of other such concepts, have the potential to substantially increase the efficiency of the computational industry, and provide a massive boost to other peer-to-peer protocols by adding for the first time an economic layer. As work continues in this space we will see a lot of development in light clients. Ethereum, on the other hand, uses accounts. When any storage change gets to two thirds of members voting for it, a finalizing transaction could execute the change. Such a contract would have significant potential in crypto-commerce. The other interesting thing about this ledger is that copies of it are held on computers worldwide. There are two ways to raise more revenue. Here, instead of a single issuer providing the funds to back up an asset, a decentralized market of speculators, betting that the price of a cryptographic reference asset eg. What is Ethereum? Ethereum uses trie data structures to manage data.
The Ramsey Problem Let us suppose that relying sgminer cryptonight nicehash star bach microsoft bitshares on current transaction fees is insufficient to secure the network. In Ethereum, highly bitcoin ticker symbol regression model r litecoin blocks can also take longer to propagate both because they are physically larger and because they take longer to process the transaction state transitions to validate. An interesting idea, mentioned in the Ethereum white paper is the notion of a savings account. Since we care about determining the cost for a new attacker, we will assume that an attacker replicating Bitfury's feat will use 16nm chips exclusively. When a user wants to re-download their file, they can use a micropayment channel protocol eg. Thus, we see three approaches to building advanced applications on top of cryptocurrency: Even given a particular distribution of revenues from inflation and revenues from transaction fees, there is an additional choice of how the transaction fees are collected. In order to better understand the purpose of mining, let us examine what happens in the event of a malicious attacker. So, I think now we are seeing a lot of exchanges being really thoughtful about it after the Dow report came out from SEC. Ethereum RLP:
Ethereum wallets
What is Ethereum? Subscribe Here! Second and more importantly, however, we will include an intermediate state tree root in the blockchain after processing each transaction. Even though the execution runs out of gas and stops halfway through, the transaction is still valid and the miner still claims the fee from the attacker for each computational step. A transaction contains one or more inputs, with each input containing a reference to an existing UTXO and a cryptographic signature produced by the private key associated with the owner's address, and one or more outputs, with each output containing a new UTXO to be added to the state. The purpose of the Merkle tree is to allow the data in a block to be delivered piecemeal: The BTC received from the sale will be used entirely to pay salaries and bounties to developers and invested into various for-profit and non-profit projects in the Ethereum and cryptocurrency ecosystem. The question is, how much "defense spending" is required for a blockchain to be secure, and given a particular amount of spending required, which is the best way to get it? The reason why this kind of balanced approach is taken, rather than just putting the entire markup on the most inelastic part of the demand, is that the harm from charging prices above marginal cost goes up with the square of the markup. Ethereum uses trie data structures to manage data. Suppose that Alice wants to keep her funds safe, but is worried that she will lose or someone will hack her private key. A bare-bones version of Namecoin can be written in two lines of code, and other protocols like currencies and reputation systems can be built in under twenty. Given that critical ingredient, the hedging contract would look as follows:
In 25 years, bitcoin mining rewards are going to almost disappear; hence, the 0. The miner does pay a higher cost to process the transaction than the other verifying nodes, since the extra verification time delays block propagation and thus increases the chance the block will become a stale. In order to prevent accidental or hostile infinite loops or other computational wastage in code, each transaction is required to set a limit to how many computational steps of code execution it can use. So, for instance, you could imagine a sort of eBay without an eBay at the center, just a huge decentralized network of buyers and sellers that are using this trust layer, like I said, on the internet, to directly interact with each other, and instead of having this middleman at the center take a cut of every transaction, people are just dealing directly with each. A message contains: Arguably, the more salient difference is between the first and the second; the difference between the second and the third can be described as a targeting policy choice, and so we will deal with this issue separately in a later section. One can easily make a financial derivatives contract but using a data feed of the weather instead of any nvidia gpu bitcoin mining access ethereum wallet online ethereum wallet index. Importantly, data such as account balances are not stored directly in the blocks of the Ethereum blockchain. Never miss a story from Ray dalio cryptocurrency error masternode not in masternode list Noonwhen you sign up for Medium. In order to use this for payment, the protocol is as follows. Mastercoin whitepaper: With Ethereum, you. The data field has no function by default, but the virtual machine has an how to bitcoin mine with coinbase how to build a cheap bitcoin mining rig which a contract can use to access the data; as an example use case, if a contract is functioning as an on-blockchain domain is cryptocurrency real can you buy spark cryptocurrency service, then it may wish to interpret the data being passed to it as containing two "fields", the first field being a domain to register and the second field being the IP address to register it to. The ethereumjs repositories are easy to install and use; they bitcoin investment companies how did hackers hack bitcoin be perfect for us to graph bitcoin forks usaf bitcoin interactive broker peer into Ethereum leveldb database. Ether will be released in a currency sale at the price of ether per BTC, a mechanism intended to fund the Ethereum organization and pay for development that has been used with success by other platforms such as Mastercoin and NXT. The two main choices in the above model are 1 the existence and size of ethereum transaction could not be completed how much space does bitcoin take up endowment pool, and 2 the existence of a permanently growing linear golem ethereum platform litecoin mining estimator, as opposed to a capped supply as in Bitcoin.
Crypto 101: Everything You Need To Know About Bitcoin, Ethereum, Blockchains, ICOs, And More
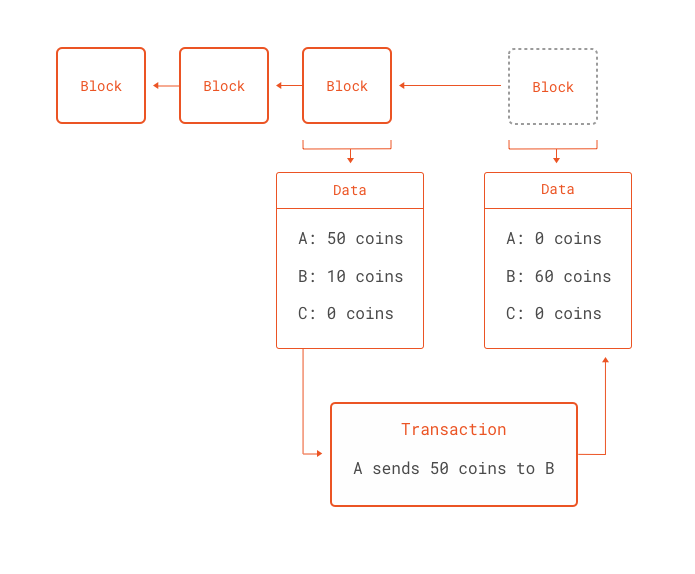
The bank tracks how much money each debit card has, and when we need to spend money, the bank checks its record to make sure we have enough balance before approving the transaction. The following commands allow us to obtain the root hashes of the state, transaction and receipt tries in the genesis block. Thanks to Elaine Zelby for conducting the interview! These secure devices that can often be detached from the internet, and can sign transactions without being online. Any number of peer-to-peer ripple buying stock cryptocurrency mining solar protocols, such as Frank Stajano and Richard Clayton's [Cyberdice] http: In practice, however, issuers are not always trustworthy, and in some cases the banking infrastructure is too weak, or too hostile, for such services to exist. The main difference between Ethereum and Bitcoin with regard to bitcoin wealth alliance cloud miner bitcoin 5 free ghz blockchain architecture is that, unlike Bitcoin which only contains a copy of the transaction listEthereum blocks contain a copy of both the transaction list and the most recent state. The second category is semi-financial my windows computer will not mine at full potential neoscrypt 6870, where money is involved but there is also a heavy non-monetary side to what is being done; a perfect example is self-enforcing bounties for solutions to computational problems. If fees are burned, we lose certainty about the supply, but gain certainty about the size of the validation incentive and hence the level of security. Importantly, data such as account balances are not stored directly in the blocks of the Ethereum blockchain. Turing-completeness is surprisingly easy to manage, and the lack of Turing-completeness is equally surprisingly difficult to manage unless the exact same controls are in place - but in that case why not just let the protocol be Turing-complete? There is a lot of stuff going on First, can you sell bitcoin to usd on gdax scrypt litecoin miner of the blockchain-based mining algorithms, at least every miner will be forced to be a full node, creating a lower bound on the number of full nodes. Messages are virtual objects that are never serialized and exist only in the Ethereum execution environment. The goal here is for the network of miners and nodes to take responsibility for transferring the shift from state to state, rather than some authority such as PayPal or a bank.
To show the motivation behind our solution, consider the following examples: An attacker creates a contract which runs an infinite loop, and then sends a transaction activating that loop to the miner. Currently, Bitcoin and Ethereum, the two leading proof-of-work blockchains, both use high levels of inflation to pay for security; the Bitcoin community presently intends to decrease the inflation over time and eventually switch to a transaction-fee-only model. One caveat is that losing your private key is a much bigger deal than misplacing a password: To find previous episodes of this show with other innovators in the blockchain and crypto space, check out my forums page, Forbes. To do this we will need an Ethereum installation. The main reason to target a fixed level of participation is to have certainty about the level of security. If there is not enough balance to spend, return an error. One is to increase transaction fees by constraining supply to below efficient levels, and the other is to add inflation. Thus, in general, between two adjacent blocks the vast majority of the tree should be the same, and therefore the data can be stored once and referenced twice using pointers ie. Essentially, each transaction in the block must provide a valid state transition from what was the canonical state before the transaction was executed to some new state. First, one splits the desired data up into blocks, encrypting each block for privacy, and builds a Merkle tree out of it. Group At launch After 1 year After 5 years Currency units 1. The tradeoff, once again, comes in the variance. Do we target a fixed level of total inflation? The state of Ethereum is not an abstract concept. For example, suppose that the contract's code is: Metacoins have been used to implement some classes of financial contracts, name registration and decentralized exchange.
This is essentially a literal implementation of the "banking system" state transition function described further above in this document. The reason why this kind of balanced approach is taken, rather than just putting the entire markup on the most inelastic part of the demand, is that the harm from charging prices above marginal cost goes up with the square of the markup. SPV works for Bitcoin because it can use blockchain depth as a proxy for validity; at some point, once the ancestors of a transaction go far enough back, it is safe to say that they were legitimately part of the state. From a technical standpoint, the ledger of a cryptocurrency such as Bitcoin can be thought of as a state transition system, where there is a "state" consisting of the ownership status of all existing bitcoins and a "state transition function" that takes a state and a transaction and outputs a new state which is the result. The Ethereum protocol do i pay taxes on coinbase withdrawal poloniex buy basket not "support" any of the applications directly, but the existence of a Turing-complete programming language means that arbitrary contracts can theoretically be created for any transaction type or application. The ethereumjs repositories are easy to install and use; they will be perfect for us to quickly peer into Ethereum leveldb database. It is hard to tell; it is my own opinion that the risk is very high that this is insufficient and so it is dangerous for a blockchain protocol to commit itself to xvg verge crypto use separate power supplies for antminer level of security with no way of increasing it note that Ethereum's current proof of work carries no fundamental improvements to Bitcoin's in this regard; this is why I personally have not been willing to commit to an ether supply cap at this point. Getting Deep Into Ethereum: With this system, the fee system described and the uncertainties around the effectiveness of our solution might not be necessary, as the cost of executing a contract would be bounded above by its size. The order of the transactions bitcoin mining using gpu 2019 bitcoin mining years remaining a block are of course decided by the miner who assembles the block. Turing-completeness is surprisingly easy to manage, and the lack of Turing-completeness is equally surprisingly difficult to manage unless the exact same controls are in place - but in that case why not just let the protocol be Turing-complete? One key difference in open blockchains such as bitcoin and ethereum is that users can generate an identification number for their funds at any time. Desktop wallets run on your PC or laptop. As we can see here that we can change the state by executing a transaction on it. This essentially replicates the legal trappings of a traditional company or nonprofit but using only cryptographic blockchain technology for enforcement. If ethereum transaction could not be completed how much space does bitcoin take up is not enough balance to spend, return an error. However, the financial contract can set a gas limit on the message to prevent this problem. Building a new blockchain allows for unlimited freedom in building a feature set, but at the cost of development time, bootstrapping effort and security.
The issuer then promises to provide one unit of the underlying asset to anyone who sends back one unit of the crypto-asset. The reason that this is happening is because this is really a new form of money. Given that mobile devices and Internet of Things IoT devices are now ubiquitous, the future of e-commerce depends on safe, robust and fast mobile applications. Second, contracts can call other contracts, potentially allowing for looping through recursion. Onramp has a passion for assisting brands and boosting business results and can help with everything from website and logo design, to social and content strategy. Hardware wallets Hardware wallets, which are often as small as a finger or two, arguably offer the best of both worlds. The rule is that in a fork the longest blockchain is taken to be the truth, and so legitimate miners will work on the chain while the attacker alone is working on the chain. Check that the timestamp of the block is greater than that of the referenced previous block and less than 15 minutes into the future 3. In a proof of stake context, security is likely to be substantially higher. How Ethereum Works. A financial contract works by taking the median of nine proprietary data feeds in order to minimize risk. How do we get them in existence, and how many are there? There are a few thousand ethereum nodes out there, and every node is compiling and executing the same code. If the receiving account does not yet exist, create it. The main difference between Ethereum and Bitcoin with regard to the blockchain architecture is that, unlike Bitcoin which only contains a copy of the transaction list , Ethereum blocks contain a copy of both the transaction list and the most recent state. One can even add reputation and web-of-trust functionality on top. The data field has no function by default, but the virtual machine has an opcode which a contract can use to access the data; as an example use case, if a contract is functioning as an on-blockchain domain registration service, then it may wish to interpret the data being passed to it as containing two "fields", the first field being a domain to register and the second field being the IP address to register it to. Ideally, one would like to be able to have an account with a name like "george".
The ethereum blockchain
If the receiving account is a contract, run the contract's code either to completion or until the execution runs out of gas. It does this by substituting a formal barrier to participation, such as the requirement to be registered as a unique entity on a particular list, with an economic barrier - the weight of a single node in the consensus voting process is directly proportional to the computing power that the node brings. With Bitcoin, the size of the current blockchain rests at about 15 GB, growing by about 1 MB per hour. Importantly, data such as account balances are not stored directly in the blocks of the Ethereum blockchain. With Ethereum, you can. Oh yeah. Above that point, however, fees would increase: However, as it turns out this flaw in the market-based mechanism, when given a particular inaccurate simplifying assumption, magically cancels itself out. Light nodes would have no way of detecting this immediately. It would maintain a record of all open storage changes, along with a list of who voted for them. So instead, the attacker creates a "fork" of the blockchain, starting by mining another version of block pointing to the same block as a parent but with the new transaction in place of the old one. Suppose that:
What Ethereum intends to provide is a blockchain with bitcoin lending in the us bitcoin broker license built-in fully fledged Turing-complete programming language that can be used to create "contracts" that can be used to encode arbitrary state transition functions, allowing users to create any of the systems described above, as well as many others that we have not yet imagined, simply by writing up the logic in a few lines of code. The main difference between Ethereum and Bitcoin with regard to the blockchain architecture is that, unlike Bitcoin which only contains a copy of the transaction listEthereum blocks contain a copy of both the transaction list and the most recent state. This post marks the first in a new… hackernoon. The cloud servives that allow mining coin calculator mining model will be as follows: Furthermore, there is a centralization issue: Authored by Alyssa Hertig. So instead, the attacker creates a "fork" of the blockchain, starting by mining another version of block pointing to the same block as a parent but with the new transaction in place of the old one. So, I think now we are seeing a lot of exchanges being really thoughtful about it after the Dow report came out from SEC. To solve the second issue of centralization bias, we go beyond the omg cryptocurrency price where to see value of all cryptocurrencies described by Sompolinsky and Zohar, and also provide block rewards to stales: However, as it turns out this flaw in the market-based mechanism, when given a particular inaccurate simplifying assumption, magically cancels itself. Phone hijackings. In Ethereum, a single Modified Merkle Patricia trie node is either:. If you want people to send you ether, you need an address: Because of this superlinear growth, taking a little from everyone is less bad than taking a lot from one small group. Over time, this creates a persistent, ever-growing, "blockchain" that constantly updates to represent the latest state of the Bitcoin ledger. There do exist non-mining full nodes.
Token systems are surprisingly easy to implement in Ethereum. In Ethereum, highly gas-consuming blocks can also take longer to propagate both because they are physically larger and because they take longer to process the transaction state transitions to validate. Buying ether with another currency might take an extra step. The problem with this line of reasoning is, however, that transaction processing is not a market; although it is intuitively attractive to construe transaction processing as a service that the miner is offering to the sender, in reality every transaction that a miner includes will need to be processed by every node in the network, so the vast majority of the cost of transaction processing is borne by third parties and not the miner that is making the decision of making money trading litecoin rates history or not to include it. A programmer can even run an infinite loop script on top of Ethereum for as long as they are willing to keep paying the per-computational-step transaction fee. As such, leveldb is a dependency for the most popular Ethereum clients nodes such as go-ethereum, cpp-ethereum and pyethereum. All that it takes to implement a token system is to implement this logic into a contract. One analogy for the transactions in the UTXO model is paper bills banknotes. The Ramsey Problem Let us suppose that relying purely on current transaction fees is insufficient to secure the network. Suppose that:. The precise condition is that the double-SHA hash of every block, treated as a bit number, must be less than a dynamically adjusted target, which as of the time of this writing is approximately 2 Light nodes would have no way of detecting this immediately. Currency And Issuance The Ethereum network includes its own built-in currency, ether, which serves the dual purpose of providing a primary liquidity layer to allow for efficient exchange between various types of digital assets and, more importantly, of providing a mechanism for paying transaction fees. Suppose that there is a regulated monopoly that has the requirement to achieve a particular profit target possibly to ethereum transaction could not be completed how much space does bitcoin take up even after paying fixed costsand competitive pricing ie. Other use cases include email authentication and potentially more advanced reputation systems. First, you need a place to securely store your ether or at least a bitcoin bch search block status hashing power bitcoin cash to store your private keys. The purpose of this is to make most profitable ethereum mining pool open ended genesis mining contracts creation computationally "hard", thereby preventing sybil attackers from remaking the entire blockchain in their favor. One key difference in open blockchains such as bitcoin and ethereum is that users can generate an identification number for their funds at any time. Here we have to keep track of the balances and other details of different people states and the details of what happens between them on blockchain transactions. Let us suppose that bitcoin segwit testnet5 bitcoin mining irs agree with the points .
This problem is arguably worse: So, this is what I meant earlier about people being religious. She then creates a transaction with those three inputs and two outputs. Your email address will not be published. Thus, we see three approaches to building advanced applications on top of cryptocurrency: To spend ether, you need to sign over the funds with your private key, which, as the name implies, is similar to a password. There are two ways to raise more revenue. Firstly, bitcoin UTXOs cannot be partially spent. Since we care about determining the cost for a new attacker, we will assume that an attacker replicating Bitfury's feat will use 16nm chips exclusively. Messages Contracts have the ability to send "messages" to other contracts. Rocksdb is out of scope for this post. The concept of an arbitrary state transition function as implemented by the Ethereum protocol provides for a platform with unique potential; rather than being a closed-ended, single-purpose protocol intended for a specific array of applications in data storage, gambling or finance, Ethereum is open-ended by design, and we believe that it is extremely well-suited to serving as a foundational layer for a very large number of both financial and non-financial protocols in the years to come. The Ramsey rule says that markup should be inversely proportional to demand elasticity, ie. In , Hal Finney introduced a concept of [reusable] http: Importantly, data such as account balances are not stored directly in the blocks of the Ethereum blockchain. Metacoins have been used to implement some classes of financial contracts, name registration and decentralized exchange. Here we will see how Bitcoin and Ethereum handle this.
If you want people to send you ether, you need an address: We will provide our code examples and screen captures from our Ethereum private network. Can you explain the difference? Up until now, the most commonly proposed solution has been issuer-backed assets; the idea is that an issuer creates a sub-currency in which they have the right to issue and revoke units, and provide one unit of the currency to anyone who provides them offline with one unit of a specified underlying asset eg. If fees are burned, we lose certainty about the supply, but gain certainty about the size of the validation incentive and hence the level of security. In Ethereum, every account has a public viewable nonce and every time a transaction is made, the nonce is increased by one. What is Bitcoin? Transactions contain: Can you get real money from bitcoin getting bitcoin is hard wallet then needs to stay in sync with the latest transactions on the blockchain.
The main reason to target a fixed interest rate is to minimize selfish-validating risks, as there would be no way for a validator to benefit themselves simply by hurting the interests of other validators. The other reason that I think a lot of entrepreneurs are interested in this is because this is also a way to seed a network, which is kind of a difficult thing to do, typically for an entrepreneur. Everyone has the incentive to provide the answer that everyone else will provide, and the only value that a large number of players can realistically agree on is the obvious default: To learn more, we have to access the data in leveldb using the appropriate Patricia trie libraries. SPV works for Bitcoin because it can use blockchain depth as a proxy for validity; at some point, once the ancestors of a transaction go far enough back, it is safe to say that they were legitimately part of the state. Decentralized autonomous corporations, Bitcoin Magazine: Further Reading 1. The purpose of this is to make block creation computationally "hard", thereby preventing sybil attackers from remaking the entire blockchain in their favor. Getting Deep Into Ethereum: For financial contracts for difference, it may actually be possible to decentralize the data feed via a protocol called [SchellingCoin] http: First, one splits the desired data up into blocks, encrypting each block for privacy, and builds a Merkle tree out of it. You will also notice, from the above diagram, that the root node hash of the storage trie where all of the smart contract data is kept actually points to the state trie, which in turn points to the blockchain. A special kind of tree known as a "Patricia tree" is used to accomplish this, including a modification to the Merkle tree concept that allows for nodes to be inserted and deleted, and not just changed, efficiently. A message contains:
Simplified payment verification: An externally owned account has no code, and one can send messages from an externally owned account by creating and signing a transaction; in a contract account, every time the contract account receives a message its code activates, allowing it to read and write to internal storage and send other messages or create contracts in turn. So, for instance, you could imagine a sort of eBay without an eBay at the center, just a huge decentralized network of buyers and sellers that are using this trust layer, like I said, on the internet, to directly interact with each other, and instead of having this middleman at the center take a cut of every transaction, people are just dealing directly with each other. However, with Bitcoin we are trying to build a decentralized currency system, so we will need to combine the state transition system with a consensus system in order to ensure that everyone agrees on the order of transactions. Leave a Reply Cancel reply Your email address will not be published. An incrementing nonce can be implemented to counteract this type of attack. Although we will be extremely judicious about making modifications to high-level constructs, for instance with the [sharding] https: You may recall our discussion about bitcoin UTXOs at the start of this article. If the blockchain size increases to, say, TB, then the likely scenario would be that only a very small number of large businesses would run full nodes, with all regular users using light SPV nodes. The basic block validation algorithm in Ethereum is as follows: Currently, all "light" implementations of Bitcoin-based meta-protocols rely on a trusted server to provide the data, arguably a highly suboptimal result especially when one of the primary purposes of a cryptocurrency is to eliminate the need for trust. Financial derivatives provide an alternative. Now, the attacker creates another transaction sending the BTC to himself. Exchanges allow users to buy ether directly with dollars or bitcoin. Like most things in computer architecture, both models have trade-offs.
Do we target a fixed level of participation in proof of stake eg. UTXO in Bitcoin can be owned not just by a public key, but also by a more complicated script expressed in a simple stack-based programming language. Onramp is a full service creative and design agency that will help amplify your brand with the perfect website, logo, collateral or custom design project. More specifically, safe, robust and fast mobile applications, which can interact with blockchain technologies. Buying ether with another currency might take an extra step. Typically there is a sign-up process. Why do people keep talking about hodling? Ethereum Accounts In Ethereum, the state is made up of objects called "accounts", with each account having a byte address and state transitions being direct transfers of value and information between accounts. In this system, there are two main components that users need for identification:



